Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Ubuntu VPS Packages and Basic Configuration Section
- Ubuntu16.04 VPS Installing Required Packages
- Ubuntu14.04 VPS Installing Required Packages
- Ubuntu12.04 VPS Installing Required Packages

Ubuntu14.04 VPS Installing Required Packages for basic and advanced configuration. Such packages and will be needed through the rest of the configuration steps. Initially, you will install and configure MTA eMail services in order to receive emails and alerts notification while you are configuring your system. The required packages will include Development Tools and packages to prepare the VM or VPS for advanced HowTo configuration Articles.
Besides, I will install updates, upgrades, NTP time server, Utilities, and Development Tools, which will prepare the VM/VPS for Linux Security Measures and Hardening Tools. As you probably noticed, the VM or the VPS must go through few layers of staging before start loading and running specific services such Web Hosting Solution services.
Objectives:
1. Installing Required Packages
2. Installing MTA eMail Services
3. Disabling AppArmor Security
4. Setting Basic Configuration
Prerequisites:
A. Basic Debian or Ubuntu System Knowledge
B. Login to your DigitalOcean or Vultr Account
C. Follow the Courses and Sections by Order
Recommendations:
For better performance, use VPS with at least 2 CPUs, 4G Memory, 1G Bandwidth, and SSD Storage drive.
Table of Contents
Installing Required Packages
Run the following steps (1 to 4)
1. Backup Source List
cp /etc/apt/sources.list /etc/apt/sources.bak
Note: or you can hold Alt-b to instruct nano editor to Backup the file before modifying and saving the file. It will save a backup of the sources.list file as “sources.list~”
Source list used to download packages for your system. DigitalOcean or Vultr might add their own sources as well to your sources.list file. I usually backup the sources.list file and I use my own list which is the default sources.list of Ubuntu14.04.
2. Edit the Source List
nano /etc/apt/sources.list
Using nano editor, I usually use Ctrl-k keys at the beginning of the file to delete all lines. Open the following sources.list, copy its content, and paste it inside the blank sources.list.
Save: Ctrl-X, Hit Y Key, and Enter.
List apt directory to see the backup file
ls -nah /etc/apt/
drwxr-xr-x 6 0 0 4.0K Feb 13 06:50 .
drwxr-xr-x 90 0 0 4.0K Feb 13 06:21 ..
drwxr-xr-x 2 0 0 4.0K Dec 10 11:39 apt.conf.d
drwxr-xr-x 2 0 0 4.0K Apr 10 2014 preferences.d
-rw-r--r-- 1 0 0 3.3K Feb 13 06:46 sources.bak
-rw-r--r-- 1 0 0 3.1K Feb 13 06:50 sources.list
drwxr-xr-x 2 0 0 4.0K Apr 10 2014 sources.list.d
-rw-r--r-- 1 0 0 13K Apr 16 2014 trusted.gpg
drwxr-xr-x 2 0 0 4.0K Apr 10 2014 trusted.gpg.d
3. Refresh Source List
apt-get update
Please make sure the source update list finish successfully, it should show you “Reading package lists… Done” with no errors, something similar to the following:
Ign http://us.archive.ubuntu.com trusty/universe Translation-en_US
Fetched 3,467 kB in 14s (244 kB/s)
Reading package lists... Done
root@ubuntu14:~#
4. Install Dependencies, Utilities, and Development Tools
Note: the following Required Packages such Dependencies, Utilities, and Development Tools are required across all the Web Hosting Solution.
TIP: Copy the whole line as one command and past it inside Putty window. Just hit right click inside Putty window after you copied the whole line below, and it should get pasted right way, then hit enter to execute.
apt-get install aptitude build-essential make module-assistant wajig libc6 libpcre3-dev libpcrecpp0 libexpat1 ssl-cert libssl-dev libpcre3 glibc-doc zlib1g-dev python-software-properties zlib1g lsb-base openssl binutils sudo arj nomarch libgeoip-dev zoo unzip zip bzip2 lzop cabextract apt-listchanges daemon libnet-ldap-perl libauthen-sasl-perl libio-string-perl git libio-socket-ssl-perl libnet-ident-perl libnet-dns-perl autoconf automake libtool flex bison debhelper binutils
Installing MTA Mail Services
I need MTA (SMTP) service such Postfix for email notification, however, Debian Base systems might come with Exim4 or Sendmail, meaning, aptitude package manager will ask you to remove other MTA packages such Exim4 or Sendmail before installing Postfix.
It’s your choice, but I highly recommend using Postfix since it’s going to be used as standard Mail Server if you decide to build Web Hosting Solution.
Run the following steps (1 to 4)
1. Install Postfix Packages
aptitude install postfix postfix-mysql postfix-doc ssl-cert
You might be prompted to remove Sendmail or Exim:
exim4-config : Conflicts: postfix but 2.9.6-2 is to be installed.
The following actions will resolve these dependencies:
Remove the following packages:
1) exim4
2) exim4-base
3) exim4-config
4) exim4-daemon-light
Accept this solution? [Y/n/q/?] y
Press Y key to continue. And confirm with Y key again.
The following packages will be REMOVED:
exim4{a} exim4-base{a} exim4-config{a} exim4-daemon-light{a}
0 packages upgraded, 10 newly installed, 4 to remove and 0 not upgraded.
Need to get 8,510 kB of archives. After unpacking 15.7 MB will be used.
Do you want to continue? [Y/n/?] y
2. Configure Postfix Settings
It should detect your FQDN.
General type of mail configuration: >> Internet Site System mail name: >> node1.ccnahub.com
3. Restart Postfix Service
service postfix restart
* Stopping Postfix Mail Transport Agent postfix [ OK ] * Starting Postfix Mail Transport Agent postfix [ OK ]
4. Forward Root Emails
nano /etc/aliases
Add your email to the end of aliases file. The file should look like this, notice the last line.
# See man 5 aliases for format
mailer-daemon: postmaster
postmaster: root
nobody: root
hostmaster: root
usenet: root
news: root
webmaster: root
www: root
ftp: root
abuse: root
noc: root
security: root
root: email@yourdomain.com
Save: Ctrl-X, Hit Y Key, and Enter.
Refresh Aliases for changes to take effect
newaliases
Disabling AppArmor Security
AppArmor is a Mandatory Access Control (MAC), and due to its complex security implementation into the kernel, I found out that it conflicts with most Web Hosting Services and Web Hosting Control Panels. For more information https://wiki.ubuntu.com/AppArmor
Note: Later on, I’ll show you how to use a crafted IPtables Script as Stateful Firewall and other Security hardening tools.
Run the following steps (1 to 5)
1. Stop AppArmor
service apparmor stop
2. Disable AppArmor Startup
update-rc.d -f apparmor remove
3. Uninstall and Remove AppArmor
aptitude remove apparmor apparmor-utils
4. Cleanup
aptitude autoclean && apt-get autoremove -y
5. Check if System Reboot Required
a. Create system-status.sh file
nano /root/system-status.sh
Copy and paste the following code inside system-status.sh file:
#!/bin/bash if [ -f /var/run/reboot-required ]; then echo ***System Reboot Required*** fi
Save: Ctrl-X, Hit Y Key, and Enter.
b. Set Execute Permission
chmod +rwx /root/system-status.sh
c. Run system-status.sh file
/root/system-status.sh
If system reboot required, you will see the following message:
***System Reboot Required***
Reboot the system anyway, since you just removed AppArmor.
Setting Basic Configuration
Run the following steps (1 to 12)
1. Change default Shell
Disable Dash as default Shell by using the following command:
dpkg-reconfigure dash
When asked: Use dash as the default system shell (/bin/sh)? Choose No
2. Install Network Time Protocol
aptitude install ntp ntpdate
Note: You might be asked to read an agreement, press q key to exit and continue.
Then set Server Time Zone
dpkg-reconfigure tzdata
Check date and time again
date
3. (Optional) For more local time accuracy, edit /etc/ntp.conf
nano /etc/ntp.conf
Scroll down to pool.ntp.org section
For Example, USA users, change ntp servers
From:
# pool.ntp.org maps to about 1000 low-stratum NTP servers. Your server will # pick a different set every time it starts up. Please consider joining the # pool: http://www.pool.ntp.org/join.html server 0.ubuntu.pool.ntp.org iburst server 1.ubuntu.pool.ntp.org iburst server 2.ubuntu.pool.ntp.org iburst server 3.ubuntu.pool.ntp.org iburst
To:
# pool.ntp.org maps to about 1000 low-stratum NTP servers. Your server will
# pick a different set every time it starts up. Please consider joining the
# pool: http://www.pool.ntp.org/join.html
server 0.us.pool.ntp.org iburst
server 1.us.pool.ntp.org iburst
server 2.us.pool.ntp.org iburst
server 3.us.pool.ntp.org iburst
Save: Ctrl-X, Hit Y Key, and Enter.
I have changed the upper pool NTP servers based on this link http://www.pool.ntp.org/zone/us just pick based on your country or area.
Restart NTP service
service ntp restart
Force Time Zone Update Using Specific NTP Server
Copy and paste all 4 lines one shot.
service ntp stop ntpdate -s us.pool.ntp.org service ntp start date
4. Display Nano Editor Cursor in the Status Bar
nano /etc/nanorc
Scroll down little bit using the arrow key, and comment out # set const in order to show Cursor Movements Line Number.
From:
# set const
To:
set const
Save: Ctrl-X, Hit Y Key, and Enter.
5. Add Warning Messages and MOTD
Very important to set Warning Messages at Web Console, SSH prompt, and Message of the Day. If an intruder penetrated your server and you are trying to get the authority involved because of data lose, first thing they would ask you “Have you set a Warning Messages and MOTD at Login Prompt?”, if not, your case will be dropped.
a. Add Web Console Message
nano /etc/issue
Copy and paste the following warning message at the end of issue file
****************************************************************** * * * - WARNING - * * * * THIS SYSTEM IS PRIVATE PROPERTY FOR * * THE USE OF AUTHORIZED USERS ONLY * * * ******************************************************************
Save: Ctrl-X, Hit Y Key, and Enter.
b. Edit MOTD file
nano /etc/motd
Copy and paste the following MOTD at the end. Before you save, edit the current MOTD message to suite your company needs. I believe, all you need to change is the company name.
****************************************************************** *** *** *** W A R N I N G ! ! ! *** *** *** *** THIS SYSTEM IS PRIVATE PROPERTY FOR THE USE OF YOUR *** *** COMPANY NAME INC. ADMIN STAFF AUTHORIZED USERS ONLY! *** *** ANY USE OF THIS COMPUTER NETWORK SYSTEM SHALL BE DEEMED *** *** TO BE EXPRESS CONSENT TO MONITORING OF SUCH USE AND TO *** *** SUCH ADDITIONAL MONITORING AS MAY BE NECESSARY TO *** *** IDENTIFY ANY UNAUTHORIZED USER. THE SYSTEM ADMINISTRATOR *** *** OR OTHER REPRESENTATIVES OF THE SYSTEM OWNER MAY MONITOR *** *** SYSTEM USE AT ANY TIME WITHOUT FURTHER NOTICE OR CONSENT. *** *** UNAUTHORIZED USE OF THIS SYSTEM AND ANY OTHER CRIMINAL *** *** CONDUCT REVEALED BY SUCH USE IS SUBJECT TO DISCLOSURE TO *** *** LAW ENFORCEMENT OFFICIALS AND PROSECUTION TO THE FULL *** *** EXTENT OF THE LAW. *** *** *** *** UNAUTHORIZED ACCESS IS A VIOLATION OF STATE AND FEDERAL, *** *** CIVIL AND CRIMINAL LAWS. *** *** *** ******************************************************************
Save: Ctrl-X, Hit Y Key, and Enter.
c. Force sshd to display Pre-Login Message
nano /etc/ssh/sshd-banner
Copy and paste the following Warning Message inside sshd-banner
****************************************************************** * * * - WARNING - * * * * THIS SYSTEM IS PRIVATE PROPERTY FOR * * THE USE OF AUTHORIZED USERS ONLY * * * ******************************************************************
Save: Ctrl-X, Hit Y Key, and Enter.
d. Edit sshd_config Configuration file
nano /etc/ssh/sshd_config
Enable Banner Message
Hit Ctrl-w and search for word banner, set as shown below. If you can’t find it, add it to the end of the file.
Banner /etc/ssh/sshd-banner
Save: Ctrl-X, Hit Y Key, and Enter.
e. Restart sshd Service
service ssh restart
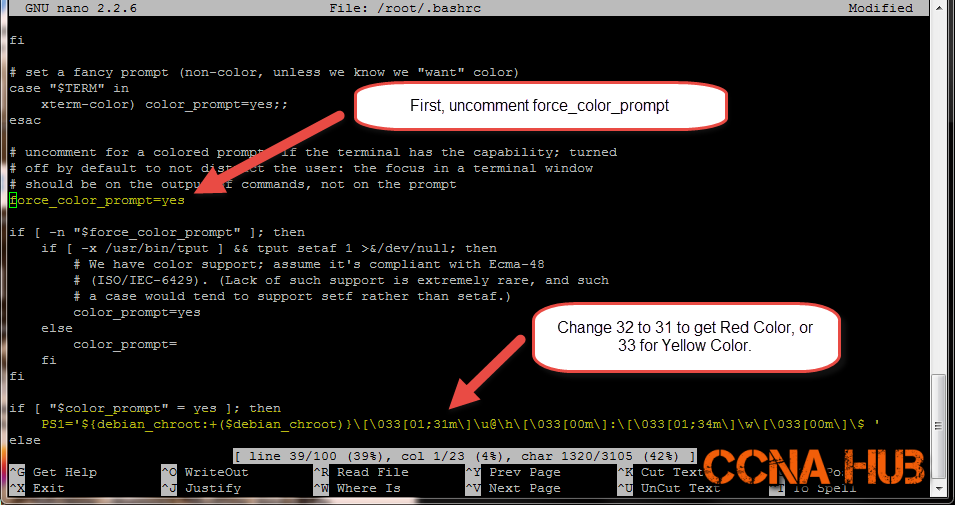
6. Change Root Prompt Color
nano /root/.bashrc
Scroll down or Ctrl-w and search for “force_color_prompt=yes“, and remove the hash sign to enable the color.
Save: Ctrl-X, Hit Y Key, and Enter.
Logout from root or Exit your Putty session; relogin to test it.
For more styling and colors, check this link https://wiki.archlinux.org/index.php/Color_Bash_Prompt
Enable Green Color Prompt for other Users
You need to comment out #force_color_prompt=yes inside the user’s .bashrc file, for example, I am going to enable green color for my user imad.
TIP: if you haven’t created extra users yet, you can use adduser command to create another user. In case you don’t want to create extra users, you can skip this step.
nano /home/imad/.bashrc
Scroll down or Ctrl-w and search for “force_color_prompt=yes“, and remove the hash sign to enable the color.
From:
# force_color_prompt=yes
To:
force_color_prompt=yes
Save: Ctrl-X, Hit Y Key, and Enter.
Test it. From root session, login as regular user
root@node1:~# login imad
Password:
You will be prompted by Green prompt
imad@node1:~$
Type exit to logout
imad@node1:~$ exit logout root@node1:~#
7. Install Package Check Tools, Reboot Notifier, and Update Notifier
aptitude install update-notifier-common debian-goodies apticron lsof
Note: the installer might ask you to read a License, press Enter then press q key to continue.
8. System and Packages Status Aliases
Run the following 2 commands:
alias packages-status="/usr/lib/update-notifier/apt-check --human-readable"
alias system-status="/usr/lib/update-notifier/update-motd-reboot-required"
Make Aliases persistent
nano .bashrc
Add the aliases to the end of .bashrc file as shown below:
[...] alias packages-status="/usr/lib/update-notifier/apt-check --human-readable" alias system-status="/usr/lib/update-notifier/update-motd-reboot-required"
Save: Ctrl-X, Hit Y Key, and Enter.
9. Install Updates and Safe Upgrades
packages-status
Note: that package-status alias points to update notifier package.
If any, you will see something similar to the following:
162 packages can be updated. 88 updates are security updates.
Now, let’s run Update and Safe Upgrades
aptitude update && aptitude -V safe-upgrade
If any updates or upgrades required, press Y key and Enter.
Note: Sometimes the apt-get cache can’t be build for some reason, a quick reboot will fix the problem. Besides, during update or upgrade, the installer might ask you to read a License, press Enter then press q key to continue.
10. Check if any of the Services needs Restart
checkrestart
Note: If you see one, two, or more services listed, then select all of them, right click again on the putty window to start all of them.
If there are some services require restart, then they will be listed as shown below:
[...]
These are the init scripts:
(restart any service get listed under this line)
service ssh restart
service ntp restart
service dbus restart
[...]
Tip: You don’t need Ctrl-c to copy content from Putty terminal, once you highlight something at putty window, it’s already copied to the Clip board. Just hit right click on the same putty window and it will be pasted on.
11. Check if System Reboot Required
system-status
Note: that system-status alias points to update notifier package.
If system reboot required, you will see the following messages
*** System restart required ***
Reboot if Required
reboot
Or Restart
shutdown -r now
TIP: -r to restart and -h to halt and Power off.
12. Run final Update and Upgrade
aptitude update && aptitude -V safe-upgrade
Subject Related
By Debian Basic Configuration | Debian Package Management | Ubuntu Basic Configuration
Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Ubuntu VPS Packages and Basic Configuration Section
- Ubuntu16.04 VPS Installing Required Packages
- Ubuntu14.04 VPS Installing Required Packages
- Ubuntu12.04 VPS Installing Required Packages

LEAVE A COMMENT