Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> CentOS VPS Packages and Basic Configuration Section
- CentOS7 VPS Installing Required Packages
- CentOS6 VPS Installing Required Packages

CentOS6 VPS Installing Required Packages for basic and advanced configuration. Such packages and will be needed through the rest of the configuration steps. Initially, you will install and configure MTA eMail services in order to receive emails and alerts notification while you are configuring your system. The required packages will include Development Tools and packages to prepare the VM or VPS for advanced HowTo configuration Articles.
Besides, I will install updates, upgrades, NTP time server, Utilities, and Development Tools, which will prepare the VM/VPS for Linux Security Measures and Hardening Tools. As you probably noticed, the VM or the VPS must go through few layers of staging before start loading and running specific services such Web Hosting Solution services.
Objectives:
1. Installing Required Packages
2. Installing MTA eMail Services
3. Disabling Firewalld and SELinux
4. Setting Basic Configuration
5. Setting Daily System Update Notifier
Prerequisites:
A. Basic Debian or Ubuntu System Knowledge
B. Login to your DigitalOcean or Vultr Account
C. Follow the Courses and Sections by Order
Recommendations:
For better performance, use VPS with at least 2 CPUs, 4G Memory, 1G Bandwidth, and SSD Storage drive.
Table of Contents
Installing Required Packages
Run the following steps (1 to 13)
1. Import Gnu Privacy Guard keys
rpm --import /etc/pki/rpm-gpg/RPM-GPG-KEY*
2. Enable Additional Repositories
First, I will make sure wget and nano editor are installed:
yum install wget nano -y
Note: Repos update their release, for instance, EPEL repo keeps updating the epel-release, meaning, as of this writing, the EPEL is epel-release-6-8.noarch.rpm, so if you face error “404 not found” while downloading the rpm, increase the version number from 6-8 to 6-9 and try again.
If you still can’t spot the right version, go to the Repo link itself at this link http://dl.fedoraproject.org/pub/epel/6/x86_64/ and search for epel-release-6, write it down and update your wget command below accordingly.
TIP: Copy the all lines in each Repo as one command and make sure all copied lines got executed. You may need to Press Enter to make sure the last line get executed. Besides, I noticed sometimes that importing (the first line) takes longer than expected, skip the first line if it takes so long.
a. Enable EPEL Repo
rpm --import https://fedoraproject.org/static/0608B895.txt wget http://dl.fedoraproject.org/pub/epel/6/x86_64/epel-release-6-8.noarch.rpm rpm -ivh epel-release-6-8.noarch.rpm
b. Enable the RPMforge
rpm --import http://dag.wieers.com/rpm/packages/RPM-GPG-KEY.dag.txt wget http://pkgs.repoforge.org/rpmforge-release/rpmforge-release-0.5.3-1.el6.rf.x86_64.rpm rpm -ivh rpmforge-release-0.5.3-1.el6.rf.x86_64.rpm
c. Enable Remi RPM Repo
rpm --import http://rpms.famillecollet.com/RPM-GPG-KEY-remi wget http://rpms.famillecollet.com/enterprise/remi-release-6.rpm rpm -ivh remi-release-6.rpm
d. Enable Psychotic Ninja RPM Repo
wget http://packages.psychotic.ninja/7/base/x86_64/RPMS/psychotic-release-1.0.0-1.el7.psychotic.noarch.rpm rpm -Uvh psychotic-release*rpm
3. Set EPEL Repo priority at 10
nano /etc/yum.repos.d/epel.repo
Make sure priority is there and set at 10, enabled=1 as shown below:
[epel] name=Extra Packages for Enterprise Linux 6 - $basearch #baseurl=http://download.fedoraproject.org/pub/epel/6/$basearch mirrorlist=https://mirrors.fedoraproject.org/metalink?repo=epel-6&arch=$basearch failovermethod=priority enabled=1 priority=10 gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-EPEL-6 [...]
Save: Ctrl-X, Hit Y Key, and Enter.
4. Set Remi Repo at priority 10
nano /etc/yum.repos.d/remi.repo
Make sure priority is there and set at 10, enabled=1 as shown below:
[remi] name=Les RPM de remi pour Enterprise Linux $releasever - $basearch #baseurl=http://rpms.famillecollet.com/enterprise/$releasever/remi/$basearch/ mirrorlist=http://rpms.famillecollet.com/enterprise/$releasever/remi/mirror enabled=1 priority=10 gpgcheck=1 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-remi failovermethod=priority [...]
Save: Ctrl-X, Hit Y Key, and Enter.
5. Set Psychotic Ninja Repo at priority 10
nano /etc/yum.repos.d/psychotic.repo
Make sure priority is there and set at 10, enabled=1 as shown below:
[psychotic] name=Psychotic Ninja Enterprise Linux Repository baseurl=http://packages.psychotic.ninja/$releasever/base/$basearch/RPMS/ enabled=1 priority=10 protect=0 gpgkey=file:///etc/pki/rpm-gpg/RPM-GPG-KEY-psychotic gpgcheck=1 [...]
Save: Ctrl-X, Hit Y Key, and Enter.
List the New Repos
You will notice that some are disabled which is fine, but make sure that the following Repos are enabled as shown below:
yum repolist all | grep -i enabled
You should have around 8 Repos enabled.
[...] base CentOS-6 - Base enabled: 6,443+132 epel Extra Packages for Enterprise Lin enabled: 12,004 extras CentOS-6 - Extras enabled: 21+29 psychotic Psychotic Ninja Enterprise Linux enabled: 85 remi Remi's RPM repository for Enterpr enabled: 3,173 remi-safe Safe Remi's RPM repository for En enabled: 0+563 rpmforge RHEL 6 - RPMforge.net - dag enabled: 3,191+1,527 updates CentOS-6 - Updates enabled: 1,166+52
6. Install Tools and Utilities
Note: the following Required Packages such Dependencies, Utilities, and Development Tools are required across all the Web Hosting Solution.
TIP: Copy the whole line as one command and past it inside Putty window. Just hit right click inside Putty window after you copied the whole line below, and it should get pasted right way, then hit enter to execute.
yum install autoconf bison flex git libtool lzop pax unzip zip yum-plugin-priorities perl bzip2 binutils bind-utils gcc make patch libgomp glibc-headers glibc-devel kernel-headers
7. Install Development Tools
yum groupinstall 'Development Tools'
8. Install Performance Tools
yum groupinstall "Performance Tools"
9. Install Network Configuration Tools
Note: If yum can’t find the system-config tools, you can skip them.
yum install system-config-network-tui system-config-firewall net-tools
10. Install Dynamic Kernel Module Support
yum install dkms -y
11. Check for kernel Updates
yum install kernel* -y
12. Check if System Reboot Required
a. Create system-status.sh file
nano /root/system-status.sh
Open the following file, copy its content to system-status.sh window.
Save: Ctrl-X, Hit Y Key, and Enter.
b. Set Execute Permission
chmod +rwx /root/system-status.sh
c. Run system-status.sh file
/root/system-status.sh
If system reboot required, you will see the following message:
***System Reboot Required***
Reboot and come back to check for updates.
reboot
13. Check for Update
yum update -y
Check System Status Again if Reboot Required
/root/system-status.sh
Installing MTA eMail Services
Run the following steps (1 to 6)
I need MTA (SMTP) service such Postfix for email notification, however, Red Hat Base systems might have Sendmail package installed, meaning, I have to disable Sendmail before installing Postfix. It’s your choice, but I highly recommend using Postfix since it’s going to be used as standard Mail Server if you decide to build Web Hosting Solution.
1. Stop Sendmail Service
service sendmail stop
If you read the following output: That means the service is not installed, go to the next step. However, if the service stopped, then execute the next command to turn sendmail off.
“sendmail: unrecognized service”
2. Disable Sendmail Startup
chkconfig sendmail off
3. Install Postfix or Double check if it’s Installed
Note: If postfix already installed, then make sure it’s started and enabled on the startup.
yum install postfix
4. Start and Enable Postfix at Startup
service postfix start
chkconfig postfix on
5. Forward Root Emails
nano /etc/aliases
Add your email to the end of aliases file. Notice the last line.
#
# Aliases in this file will NOT be expanded in the header from
# Mail, but WILL be visible over networks or from /bin/mail.
#
# >>>>>>>>>> The program "newaliases" must be run after
# >> NOTE >> this file is updated for any changes to
# >>>>>>>>>> show through to sendmail.
#
# Basic system aliases -- these MUST be present.
mailer-daemon: postmaster
postmaster: root
[...]
# Person who should get root's mail
root: email@yourdoamin.com
Save: Ctrl-X, Hit Y Key, and Enter.
Refresh Aliases for changes to take effect
newaliases
6. Finally, restart Postfix
service postfix restart
Shutting down postfix: [ OK ] Starting postfix: [ OK ]
Disabling Firewall and SELinux
SELinux is a Mandatory Access Control (MAC), and due to its complex security implementation into the kernel, I found out that it conflicts with most Web Hosting Services and Web Hosting Control Panels. For more information https://wiki.centos.org/HowTos/SELinux
Note: Later on using course4, I’ll show you how to use a crafted IPtables Script as Stateful Firewall and other Security hardening tools.
Run the following steps (1 to 5)
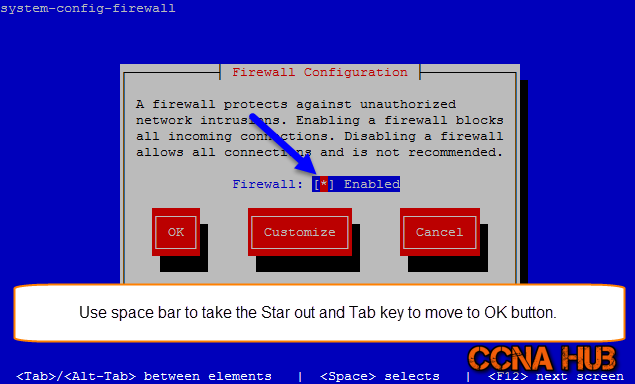
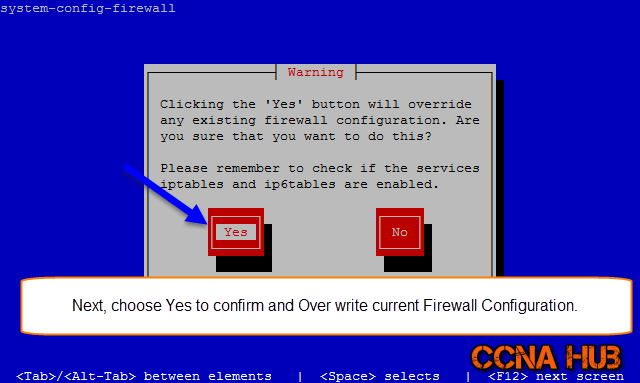
1. Disable System Firewall
system-config-firewall
Note: Remove the Star to disable the Firewall.
2. Check Firewall IP v4 and v6 Rules
iptables -L
Make sure are empty, should look as follows:
Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
And IPv6 Firewall
ip6tables -L
Chain INPUT (policy ACCEPT) target prot opt source destination Chain FORWARD (policy ACCEPT) target prot opt source destination Chain OUTPUT (policy ACCEPT) target prot opt source destination
3. Enable IPtables at Startup
chkconfig iptables on
chkconfig ip6tables on
4. Edit SELinux Config File
nano /etc/selinux/config
Disable it as shown below:
Note: You might see it disabled already, however, verify. Besides, you might see blank file, that means is not installed; in either case hit Ctrl-x to exit and continue.
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled
# SELINUXTYPE= can take one of these two values:
# targeted - Targeted processes are protected,
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
Save: Ctrl-X, Hit Y Key, and Enter.
Note: no need to reboot if SELinux already disabled.
5. Check if System Reboot Required
/root/system-status.sh
If SELinux, was enabled and you disabled it, then you must reboot for changes to take effect.
Setting Basic Configuration
Run the following steps (1 to 8)
1. Display Nano Editor Cursor in the Status Bar
nano /etc/nanorc
Scroll down little bit using the arrow key, and comment out # set const in order to show Cursor Movements Line Number.
From:
# set const
To:
set const
Or You might find using Fedora as:
set constantshow
Save: Ctrl-X, Hit Y Key, and Enter.
2. Install Network Time Protocol
yum install ntp
Configure ntp on Startup
chkconfig ntpd on
Start NTP Service
service ntpd start
Starting ntpd: [ OK ]
3. Set Time Zone
There are 2 choices to change the Time Zone, either using a Menu Driven way, or Manually Change/Set the Time Zone.
Time Zone Menu Driven
tzselect
Finally, you will be prompted to confirm your time:
Therefore TZ='America/New_York' will be used. Local time is now: Thu Jun 2 16:08:05 EDT 2016. Universal Time is now: Thu Jun 2 20:08:05 UTC 2016. Is the above information OK? 1) Yes 2) No
Then Check the Date
date
The date command output should show you Local time
Thu Jun 2 16:12:51 EDT 2016
Note: If the date command showing you Universal Time instead of Local Time, then set your time manually using the below steps.
Set your VPS time Manually
a. Pick your time zone from
https://en.wikipedia.org/wiki/List_of_tz_database_time_zones
b. Backup the current time zone
cp /etc/localtime /root/old.timezone
c. Remove the current time and confirm
rm /etc/localtime
rm: remove regular file `/etc/localtime’? yes
d. Set the New time zone based on the upper wikipedia link
ln -s /usr/share/zoneinfo/America/New_York /etc/localtime
e. Check your time
date
You should see the Local time.
4. (Optional) For more local time accuracy, edit /etc/ntp.conf
nano /etc/ntp.conf
Scroll down to pool.ntp.org section
For Example, USA users, change ntp servers
From:
# Use public servers from the pool.ntp.org project. # Please consider joining the pool (http://www.pool.ntp.org/join.html). server 0.centos.pool.ntp.org iburst server 1.centos.pool.ntp.org iburst server 2.centos.pool.ntp.org iburst server 3.centos.pool.ntp.org iburst
To:
# Use public servers from the pool.ntp.org project.
# Please consider joining the pool (http://www.pool.ntp.org/join.html).
server 0.us.pool.ntp.org iburst
server 1.us.pool.ntp.org iburst
server 2.us.pool.ntp.org iburst
server 3.us.pool.ntp.org iburst
Save: Ctrl-X, Hit Y Key, and Enter.
I have changed the upper pool NTP servers based on this link http://www.pool.ntp.org/zone/us just pick based on your country or area.
Restart NTP service
service ntpd restart
Shutting down ntpd: [ OK ] Starting ntpd: [ OK ]
Force Time Zone Update Using Specific NTP Server
Copy and paste all 4 lines one shot.
service ntpd stop ntpdate -s us.pool.ntp.org service ntpd start date
5. Add Warning Messages and MOTD
Very important to set Warning Messages at Web Console, SSH prompt, and Message of the Day. If an intruder penetrated your server and you are trying to get the authority involved because of data lose, first thing they would ask you “Have you set a Warning Messages and MOTD at Login Prompt?”, if not, your case will be dropped.
a. Add Web Console Message
nano /etc/issue
Copy and paste the following warning message at the end of issue file
****************************************************************** * * * - WARNING - * * * * THIS SYSTEM IS PRIVATE PROPERTY FOR * * THE USE OF AUTHORIZED USERS ONLY * * * ******************************************************************
Save: Ctrl-X, Hit Y Key, and Enter.
b. Edit MOTD file
nano /etc/motd
Copy and paste the following MOTD at the end. Before you save, edit the current MOTD message to suite your company needs. I believe, all you need to change is the company name.
****************************************************************** *** *** *** W A R N I N G ! ! ! *** *** *** *** THIS SYSTEM IS PRIVATE PROPERTY FOR THE USE OF YOUR *** *** COMPANY NAME INC. ADMIN STAFF AUTHORIZED USERS ONLY! *** *** ANY USE OF THIS COMPUTER NETWORK SYSTEM SHALL BE DEEMED *** *** TO BE EXPRESS CONSENT TO MONITORING OF SUCH USE AND TO *** *** SUCH ADDITIONAL MONITORING AS MAY BE NECESSARY TO *** *** IDENTIFY ANY UNAUTHORIZED USER. THE SYSTEM ADMINISTRATOR *** *** OR OTHER REPRESENTATIVES OF THE SYSTEM OWNER MAY MONITOR *** *** SYSTEM USE AT ANY TIME WITHOUT FURTHER NOTICE OR CONSENT. *** *** UNAUTHORIZED USE OF THIS SYSTEM AND ANY OTHER CRIMINAL *** *** CONDUCT REVEALED BY SUCH USE IS SUBJECT TO DISCLOSURE TO *** *** LAW ENFORCEMENT OFFICIALS AND PROSECUTION TO THE FULL *** *** EXTENT OF THE LAW. *** *** *** *** UNAUTHORIZED ACCESS IS A VIOLATION OF STATE AND FEDERAL, *** *** CIVIL AND CRIMINAL LAWS. *** *** *** ******************************************************************
Save: Ctrl-X, Hit Y Key, and Enter.
c. Force sshd to display Pre-Login Message
nano /etc/ssh/sshd-banner
Copy and paste the following Warning Message inside sshd-banner
****************************************************************** * * * - WARNING - * * * * THIS SYSTEM IS PRIVATE PROPERTY FOR * * THE USE OF AUTHORIZED USERS ONLY * * * ******************************************************************
Save: Ctrl-X, Hit Y Key, and Enter.
d. Edit sshd_config Configuration file
nano /etc/ssh/sshd_config
Enable Banner Message
Hit Ctrl-w and search for word banner, set as shown below. If you can’t find it, add it to the end of the file.
Banner /etc/ssh/sshd-banner
Save: Ctrl-X, Hit Y Key, and Enter.
e. Restart sshd Service
service sshd restart
6. Change Root Prompt Color
nano /root/.bashrc
Open the following file, add either Red or yellow code to the end of .bashre file
Note: for security reason, wordpress doesn’t show codes carry back slashes, therefore, I had them in a text file.
Save: Ctrl-X, Hit Y Key, and Enter.
Logout from root or Exit your Putty session; relogin to test it.
[root@node1 ~]#
For more styling and colors, check this link https://wiki.archlinux.org/index.php/Color_Bash_Prompt
Enable Green Color Prompt for other Users
Open the file again and add the Green color at the end of any user’s .bashrc file. For example, I am going to enable green color for my user imad.
TIP: if you haven’t created extra users yet, you can use adduser command to create extra user and passwd to set a password for that user. In case you don’t want to create extra users, you can skip this step.
nano /home/imad/.bashrc
Save: Ctrl-X, Hit Y Key, and Enter.
Login as regular user:
[root@node1 ~]# su -l imad imad@node1:~$ exit logout [root@node1 ~]#
Setting Daily System Update Notifier
I would like to have the system email me everyday if updates available. There are 2 ways I know of to notify me about if System updates are available on CentOS 6.7. Either install yum-cron or simply configure yum check-update result to be emailed daily as notifier.
yum-cron is toward putting the system update on auto pilot with no System Admin intervention, however, I would like to always have the chance to backup or look at the list of updates before updating, therefore, I won’t use the auto update feature of yum-cron, but of course, I will use it to email me with a list of needed updates.
Run the following steps (1 to 4)
1. Install Yum Cron
yum install yum-cron
2. Configure Yum Cron
nano /etc/sysconfig/yum-cron
Mine looks as follows. I am showing only the modified fields.
# Don't install, just check (valid: yes|no) CHECK_ONLY=yes # Check to see if you can reach the repos before updating (valid: yes|no) CHECK_FIRST=yes # by default MAILTO is unset, so crond mails the output by itself # example: MAILTO=root MAILTO=email@yourdomain.com
Save: Ctrl-X, Hit Y Key, and Enter.
3. Put yum-cron on Startup
chkconfig yum-cron on
4. Start yum-cron Service
service yum-cron start
That’s it! You should be able to receive daily System updates after the Email Server is configured.
Yum Update Email Notifications
If you would like to receive update Notification, it can be configured with yum check-update output as daily email.
Simple Yum Check Update Email Notification
nano /etc/cron.daily/yum-check-updates.cron
Add the following Daily Yum Update Check inside yum-check-updates.cron file
#!/bin/sh /usr/bin/yum check-update 2>&1 | /bin/mail -s "yum check-update output" root
Change the File Permission
chmod +rwx /etc/cron.daily/yum-check-updates.cron
List cron.daily Directory, all files should be Green Color
ls -lah /etc/cron.daily/
[...] -rwxr-xr-x 1 root root 4.9K Jul 24 06:27 0yum.cron -rwx------. 1 root root 180 Jul 9 2003 logrotate -rwxr-xr-x 1 root root 87 Sep 27 23:29 yum-check-updates.cron
root at the end, indicates that the result will be sent to root, and since you configured aliases above, root emails will be sent to the email you specified. Keep in mind that you won’t receive any updates right now since the email server has not been configured yet.
Let’s Check Yum Updates Again
yum update -y
Check if System Reboot Required
/root/system-status.sh
Subject Related
By Godaddy Initial CentOS Setup | HowToForge CentOS Initial Setup
Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> CentOS VPS Packages and Basic Configuration Section
- CentOS7 VPS Installing Required Packages
- CentOS6 VPS Installing Required Packages

LEAVE A COMMENT