CCNA Routing and Switching
<< IP and Network Fundamentals Course
>> Models, Protocols, and Standards Section
- Understanding TCP/IP and OSI Models
- Understanding Packet Flow Across the Network Part1
- Understanding Packet Flow Across the Network Part2
- Understanding Ethernet LAN Standards
- Understanding Ethernet MAC Addresses
- Understanding WAN Technologies
- Understanding Data Link Layer Encapsulation
- Understanding EoMPLS WAN Technology
- Understanding IP Routing Process Concept
- Understanding Web Browser DNS Lookup
- Understanding ARP Broadcast Message
- Understanding TCP and UDP Protocols
- Understanding TCP and UDP Multiplexing
- Understanding Application Layer Services
- Understanding Quality of Service Concept

Understanding TCP and UDP Protocols help you understand Transport Layer Functions. Having said this, two major protocols located at Transport Layer. 1) Transmission Control Protocol (TCP) which it’s a Connection Oriented Protocol, 2) User Datagram Protocol (UDP) which is Connectionless Protocol. These protocols are the backbone of Segmentation process. TCP and UDP are the most famous protocols at Transport Layer, they determine the method how IP packets at the next Layer should be delivered.
Table of Contents
TCP and UDP Features
As I mentioned about “Post Office Concept” under Understanding Packet Flow Across the Network Part1, TCP or UDP are very similar to the Postal Delivery Services. TCP can be similar to Postal Guarantee Mail Delivery feature which available if the customer asked for it.
In TCP/IP suite, any running service or application can ask for Guarantee Delivery feature if needed by using Transmission Control Protocol (TCP) during their TCP Socket initiation. So, in order to understand such Guarantee Delivery feature, you need to ask yourself: why do I need Guarantee Mail Delivery if I use the Post Office?
Well, there are too many obstacles on the way while the Post Office is trying deliver your Mail or package, E.g. weather, road construction, human error, priorities, politics involved, and much more. Paying more for Guarantee Mail Delivery, list your mail or package on the priority list, therefore, guaranteeing your mail delivery.
With TCP Error Recovery feature, it cost more processing to redeliver each lost or dropped frame, therefore, it’s very crucial to guarantee delivery for too many services such file transfer. However, modern equipment got more processing which is not an issue, yet TCP can’t be used across all services, you will read later on why TCP can’t be used instead of UDP especially when voice Apps used.
TCP provides its features for Upper Layers by:
1. Reliable transmission and Error Recovery – using a sequence number to identify each byte of data, therefore, will be able to retransmit the TCP Segments if it lost during Frame transmission.
2. Flow and Congestion control – Avoiding Congestion possible by controlling the rate of data entering the network (a NIC card or Port) keeping the data flow below a rate where it might trigger a collapse known by Buffer Overflow (where the OS crashes, freezes, or restart).
3. TCP’s Error Recovery – Since Data Segments are received and sent based on Sequence Numbers, if a frame get dropped or lost on the way, it resends the lost data based on a Sequence Number(s) that was lost along the frame.
4. TCP’s Data Flow – through Congestion Control “TCP Data Window Sizing Management”, in case the remote computer is limited to receive or send certain amount of Data, TCP adjusts the window based on NIC or port/media’s Speed and Duplex.
Why TCP is Crucial?
Hosts and Routers Data Link Layer Protocols notice frame errors through Frame Check Sequence (FCS) and discard frames for many reasons, including bit errors and congestion. However, FCS only and only discard, it’s the job of TCP’s Error Recovery feature to re-transmit the lost packets (dropped frames).
UDP: does not provide Error Recovery and Flow Control, but it doesn’t mean that UDP has no major role in some applications’ needs. The good thing about UDP that it needs fewer bytes in its header compared to TCP Header, resulting in fewer bytes of overhead in the network. UDP light weight header used for application such VoIP, Video, and gaming where it needs neither error recovery nor flow control.
Port Numbers: How do applications choose between TCP and UDP services? Based on Port Number Type picked, either TCP or UDP Port type can be used. Usually Service’s Applications are configured to pick the right type of port, either TCP or UDP port. Most of the time a port number determine whether a TCP or UDP features are being used by the application or service.
Using TCP Features
Applications developers free to choose either TCP or UDP based on their application’s needs. TCP provides error recover but with price (resources), it consumes more bandwidth and uses more CPU processing cycle. UDP uses less CPU and bandwidth, but it does not perform Error Recovery or Flow Control. It depends on the application needs.
Note: No matter what protocol the application is using TCP or UDP, understanding the logic behind each one is very crucial for Router ACL and Firewall Rules configuration.
TCP Features Table
TCP accomplishes the features listed above through processes located at the endpoint computers. Meaning, both PC1 and the Web Server work together based on TCP logic functions to deliver the right data. As mentioned on TCP/IP Model Article, TCP main role is to service the application needs before Layer 3 packet (package) the data for delivery, TCP relies on internet protocol (IP) layer 3 for end-to-end to deliver the segmented data, and it doesn’t really care how IP layer 3 will do it through the other layers.
In addition, IP Routing will deliver more precisely to the right remote Server’s Service or Application once TCP is used, because of the combination of TCP features and the Port number being used. Transport Layer 4 rely on IP (Layer 3) for delivery, so network devices performs TCP features the same way if they are connected to LAN, WAN, or even separated by the entire Internet. TCP segments have no idea about the LAN, WAN, or even Satellite signals since it’s packed inside an IP Packet.
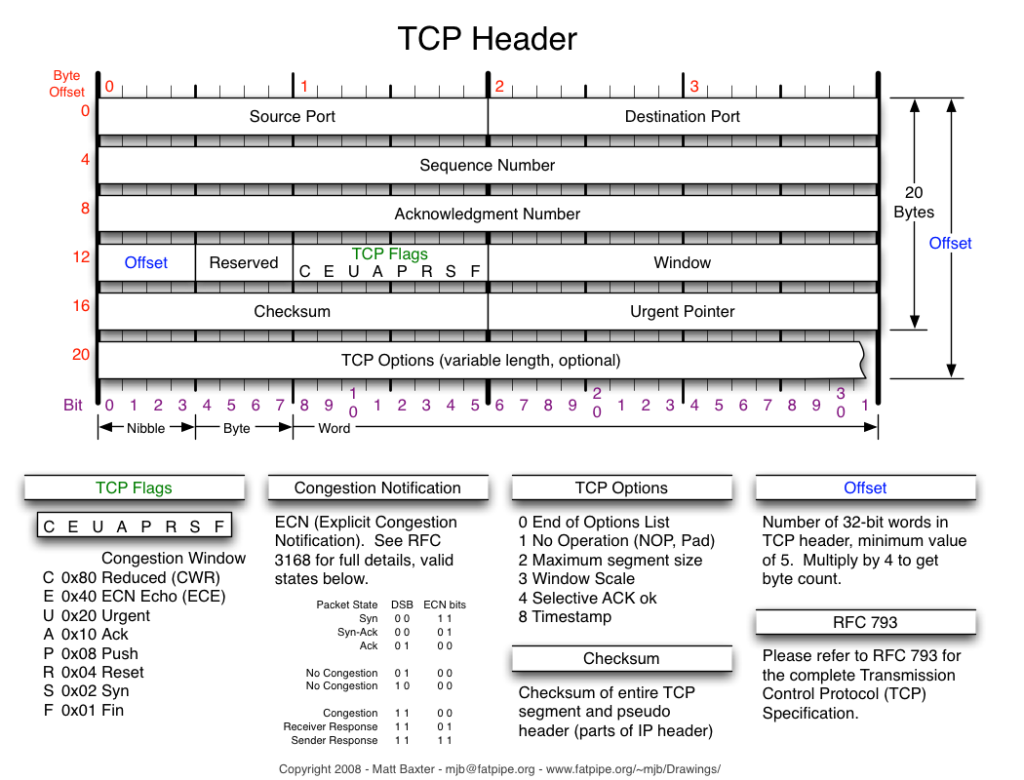
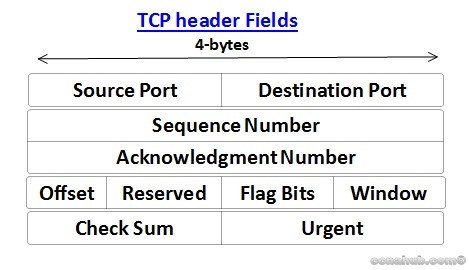
TCP Header Structure
TCP header Simplified
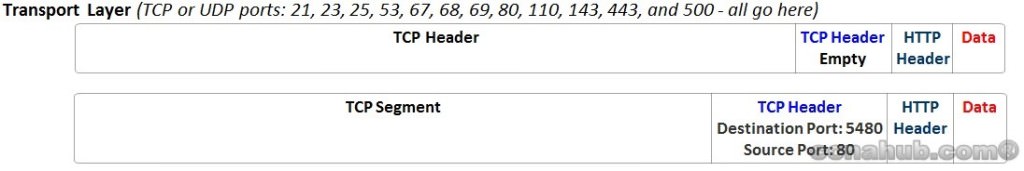
TCP begins with TCP header and followed by any application data is called TCP Segment or it’s called L4PDU by OSI model.
TCP 3 Way Hand Shake
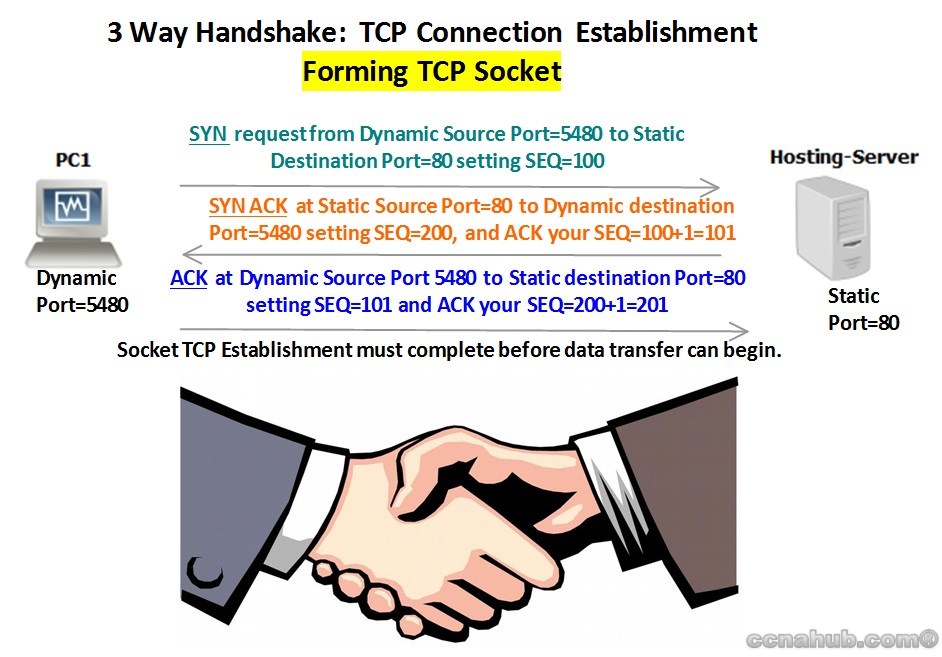
TCP Connection Establishment and Termination distinguish it than UDP function. The process of “3 way Handshake” which provide Reliability meant only for TCP. In order to transfer a web page from the web server to PC1, TCP at PC1 and the TCP at the web server both establish a connection based on sequence numbers followed by acknowledgments.
To establish a connection, TCP on both sides uses 3 ways handshake, therefore, before a client form a socket with the web server, the server must first bind to and listen at a TCP port type 80 to open it up for connections.
Starting by PC1, to establish a connection, the three-way handshake occurs as follows:
1. SYN: PC1 sends a SYN with Dynamic source TCP Port type e.g. 5480 to the Web Server or Hosting Server with segment’s sequence number at random value, e.g. 100.
2. SYN-ACK: In response, the Hosting Server replies with a SYN-ACK. The acknowledgment number is set to one more than the received sequence number i.e. 100+1, and the sequence number that the Hosting Server chooses for the respond packet is another random number, e.g. 200.
3. ACK: Finally, PC1 sends an ACK back to the Hosting Server. The sequence number is set to the received acknowledgement value of 101, and the acknowledgement number is set to one more than the received sequence number value of 200+1.
At this point, both PC1 and the Hosting Server have acknowledged the connection. From step 1 up to step 2 the communication has been established the connection parameter and a sequence number was set and acknowledged for one direction.
Then from step 2 again up to step 3, the communication has continued to establish the rest of the connection parameter with another sequence number for the other direction, and it was acknowledged.
Note: with the upper steps, a Full-Duplex communication has been established and both devices ready to transfer data, meaning, they are ready to send and receive at the same time from each other.
SYN and ACK Flags – SYN means “Synchronize the Sequence Number” and ACK means Acknowledging the SEQ number and adding number 1.
TCP Connection Termination happens with 4 Way Handshake.
To close a TCP session, an extra Flag is used FIN (Finish).
1. ACK, FIN: When PC1 has no more data to send in the stream, it sends a segment with the FIN flag set.
2. ACK: The Hosting Server sends an ACK flag to acknowledge the receipt of the FIN flag, therefore, prepares to terminate the session.
3. ACK, FIN: The Hosting Server sends a FIN flag to PC1, indicating that the session will be terminated.
4. ACK: PC1 responds with an ACK flag, acknowledging the FIN flag and terminate the session.
A server or client can start a FIN flag and it’s possible to terminate the session by 3 ways Handshake as well, FIN, ACK FIN, and finally FIN. So TCP establishes and terminates TCP sockets connection between network devices, whereas UDP doesn’t use establishing method, hence, a TCP is Connection Oriented and UDP is a Connectionless to further explain the difference between TCP and UDP Protocols.
Why TCP is Connection Oriented Protocol?
A protocol that requires an exchange of messages such SYN, ACK, and FIN before data transfer or needs pre-established requirements (similar to Handshake) between 2 network devices, will be considered “Connection Oriented Protocol”, therefore, TCP is a Connection Oriented Protocol.
User Datagram Protocol (UDP)
The only similar feature between UDP and TCP is Port Multiplexing feature, that’s it; it doesn’t provide any extra features to running Services or Application like TCP features do.
UDP is a Connectionless protocol, no Establishment Requirements, no Error detection, no Flow control, nor Congestion control, yet,it has perfect properties for certain running Services or Application; it is a must for certain application where overhead on TCP is not acceptable.
UDP is only 4-byte header comparing with 20-byte TCP header, which makes UDP very light protocol. A number of UDP’s attributes make it especially suited for certain applications where it doesn’t need all features that TCP provides.
The UDP Attributes are:
1. It is Connectionless, suitable for simple query-response such Domain Name System (DNS) or Network Time Protocol (NTP)
2. It provides datagrams: meaning no delivery guarantee is needed, that makes it suitable IP tunneling, Remote Procedure Call, and up to Network File System version 3. NFSv4 uses both TCP and UDP.
3. It is simple, suitable for bootstrapping (Network Booting) such DHCP and TFTP.
4. It is Stateless, and due to less overhead, suitable for very large numbers of clients where streaming media applications is serviced such IPTV or YouTube channels.
5. The Lack of Error Detection features perfect to avoid retransmission delay, suitable for real-time application such VoIP, Online Games, and many protocols built on top of the Real Time Streaming protocol (RTSP).
6. Works well in Unidirectional Communication, suitable for broadcast information such in many kinds of service discovery and shared information like broadcast time or Routing Information Protocol (RIP).
The following shows UDP Table and UDP Header and as you can see from the table below, UDP requires less processing and it is the main player with too many applications where Error Recovery and Flow Control is not needed in terms of Media Streaming or not acceptable in terms of Real-time application such VoIP.
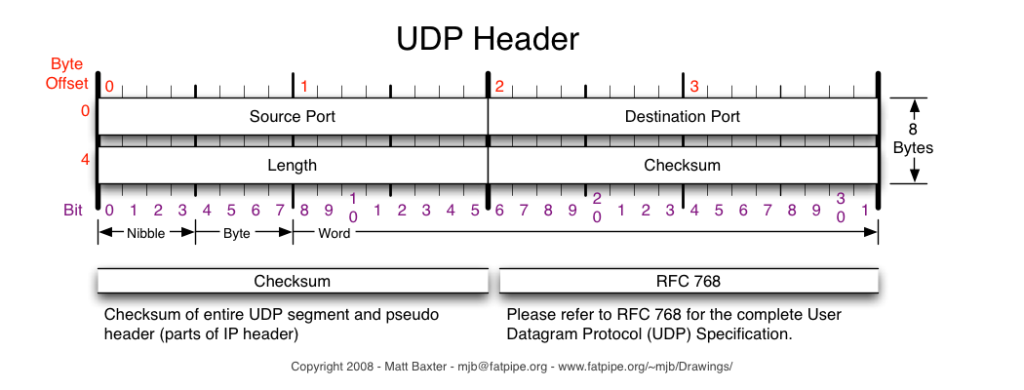 Why UDP is Connectionless Protocol?
Why UDP is Connectionless Protocol?
A protocol that does not need an exchange of messages like TCP’s handshake does, and it has no pre-established requirements such agreeing on set of rules before starting the data transfer process, hence, considered a “Connectionless Protocol”.
By the way, and in Routing Protocols world, OSPF is considered as Connection Oriented Protocol and RIP is considered Connectionless Protocol.
TCP/UDP Port Numbers Range
Well Known Ports (Numbers 0 to 1023) – These numbers are reserved for services on the Server side. They are commonly used for services such as HTTP (web server) POP3/SMTP (e-mail server) and Telnet. By defining these well-known ports for services ONLY, client applications can be programmed to request a connection to that specific port and its associated service.
Registered Ports (Numbers 1024 to 49151) – These port numbers are assigned to user processes or applications. These processes are primarily individual applications that a user has chosen to install rather than common applications that would receive a Well Known Port. When not used for a server resource, these ports may also be used dynamically selected by a client as its source port.
Dynamic or Private Ports (Numbers 49152 to 65535) – Also known as Ephemeral Ports, these are usually assigned dynamically to client applications when initiating a connection. It is not very common for a client to connect to a service using a Dynamic or Private Port (although some peer-to-peer file sharing programs do).
Subject Related
By Wikipedia TCP and UDP | Router Ally TCP and UDP | HighTech Layer 4 | How to Master CCNA | Cisco CCNA Simplified | Cisco CCNA in 60 Days | TCP Sockets | CCNA R&S Study | R&S 200-120 Official Guide | Routing and Switching Guide
CCNA Routing and Switching
<< IP and Network Fundamentals Course
>> Models, Protocols, and Standards Section
- Understanding TCP/IP and OSI Models
- Understanding Packet Flow Across the Network Part1
- Understanding Packet Flow Across the Network Part2
- Understanding Ethernet LAN Standards
- Understanding Ethernet MAC Addresses
- Understanding WAN Technologies
- Understanding Data Link Layer Encapsulation
- Understanding EoMPLS WAN Technology
- Understanding IP Routing Process Concept
- Understanding Web Browser DNS Lookup
- Understanding ARP Broadcast Message
- Understanding TCP and UDP Protocols
- Understanding TCP and UDP Multiplexing
- Understanding Application Layer Services
- Understanding Quality of Service Concept


Thanks very much, this article really helps me understand scenarios of udp and tcp Protocol.