CCNA Routing and Switching
<< IP and Network Fundamentals Course
>> Models, Protocols, and Standards Section
- Understanding TCP/IP and OSI Models
- Understanding Packet Flow Across the Network Part1
- Understanding Packet Flow Across the Network Part2
- Understanding Ethernet LAN Standards
- Understanding Ethernet MAC Addresses
- Understanding WAN Technologies
- Understanding Data Link Layer Encapsulation
- Understanding EoMPLS WAN Technology
- Understanding IP Routing Process Concept
- Understanding Web Browser DNS Lookup
- Understanding ARP Broadcast Message
- Understanding TCP and UDP Protocols
- Understanding TCP and UDP Multiplexing
- Understanding Application Layer Services
- Understanding Quality of Service Concept

Understanding TCP/IP and OSI Models will help you visualize how Network Protocols work together to establish Network connections among network devices and be able to exchange information. There are too many ways to understand TCP/IP and OSI Modules concept, the most known way is to compare or map the modules to Post Office’s departments since the Layers can be so similar to each other in terms of Routing, Packaging, and Processing functionalities.
So, mapping how the the Post Office’s Departments work all together to process a Letter or Package, will help you understand each Layer’s functions, however, I am not saying that it’s totally the same, but will make it easy to grasp the concept.
Table of Contents
TCP/IP and OSI in Brief
TCP/IP and OSI are hierarchical models to define how network devices and their applications must follow Protocols that have set of rules in order to communication with each other, similar to People Laws such a country Constitution.
Transmission Control Protocol/Internet Protocol (TCP/IP) Model was created by US Department of Defense (DOD) and Open Systems Interconnect (OSI) model was created by the International Standards Organization (ISO).
So, a Network Model such TCP/IP or OSI refers to comprehensive set of Protocols. Those protocols which are set of logical rules that Network devices must follow to communicate with each other. Protocols such HTTP, FTP, SMTP, POP3, OSPF, EIGRP, and ARP, just to name a few.
Important of TCP/IP and OSI Models
By understanding the TCP/IP and OSI models, you can imagine how TCP/IP protocols manage IP network flow.
- On the downstream, how bits are sent by a network devices as electrical pulse across copper wires or pattern of light signals across fiber optic wires.
- On the upstream how those bits received by a network device’s layer 1, reassembled into frame, de-encapsulated and re-encapsulated back again with New MAC address or switched to the right destination through the Ethernet switch.
- On the Host/PC’s upstream, how those bits received from a switch or another Network device, disassembled the frame and the packet to verify if it’s meant to its MAC or IP address; how the Host/PC’s TCP/IP Stack breaks up the segment at the transport layer, responds with an acknowledgement (ACK), and sends the data up to the session, presentation, and application layers; and how every tiny communication requires this whole process to happen in a fraction of a second!
Pretty cool, huh? This process will make more sense to you after reading few articles of IP Fundamentals.
TCP/IP Suite Overview
Transmission Control Protocol/Internet Protocol (TCP/IP). The first part: TCP is a main protocol that runs under Transport Layer 4 of TCP/IP Model; IP is another main protocol that runs under Network Layer 3 of TCP/IP Model, hence, called TCP/IP Network Model – they just picked its name based on those protocols.
Both of them combined; refer to the whole suite or Networking Model that is used today for Network communication. OSI is similar to TCP/IP and used globally as reference Model since it has 7 layers vs. 5 Layers used by TCP/IP Model. But remember, we configure IPv4 or IPv6 stack on the Network devices instead of OSI stack.
The TCP/IP Networking Model defines and references a large collection of protocols that allow components to communicate. To help people understand a networking model (such TCP/IP and OSI Models), each model broken down to something called Layers. Each layer includes protocols and standards that relate to that category of functions and TCP/IP has two models as shown below.
The original TCP/IP Network Model started with 4 Layers
4. Application
3. Transport
2. Internet
1. Link Layer
The second version of TCP/IP became 5 layers: changed the name of Internet Layer to Network layer and divided the link Layer to 2 layers
5. Application
4. Transport
3. Network
2. Data-Link
1. Physical
The difference between OSI model and TCP/IP model: OSI stretched Application layer to 2 more layers:
7. Application
6. Representation
5. Session
4. Transport
3. Network
2. Data-Link
1. Physical
TCP/IP Model – 5 Layers
Application Layer (5)
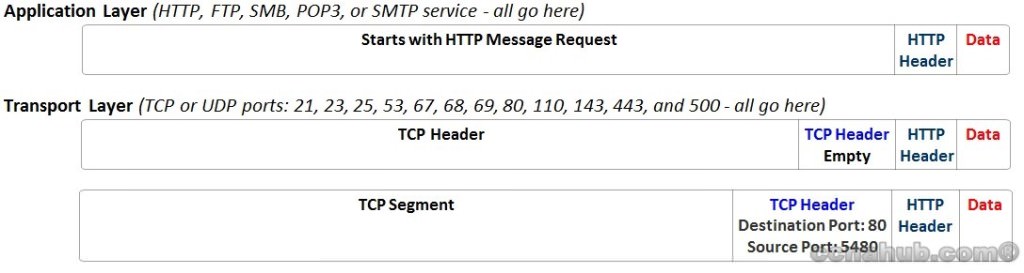
The TCP/IP Application Layer protocols provide services to the application software running on a PC or Server such HTTP, FTP, SMTP, POP3, and much more. The application layer does not define the application itself, but it defines services that applications need. E.g. application HTTP defines how web browsers can pull the contents of a web page from a web server, therefore, the application layer provides an interface between a browser running on a PC and a web services running on a web server.
Representation Overview as Part of App Layer: The TCP/IP Representation Layer part of the Operating System level where it converts incoming and outgoing data stream to represent it in a specific file format using a specific window such text, jpeg, and html window with the help of its appropriate program. In addition, data encryption happens at this layer as well since that’s where it can be represented.
Note: that the Presentation Layer at TCP/IP Model is a feature included with Application Layer.
Session Overview as Part of App Layer: The TCP/IP Session Layer can be considered the manager of session between the PC and a remote PC or Server from setting up, coordinate, terminate, exchange, and manage the application sessions from starting point to the end point.
Note: that the Session Layer at TCP/IP Model is a feature included with Application Layer.
Transport Layer (4)
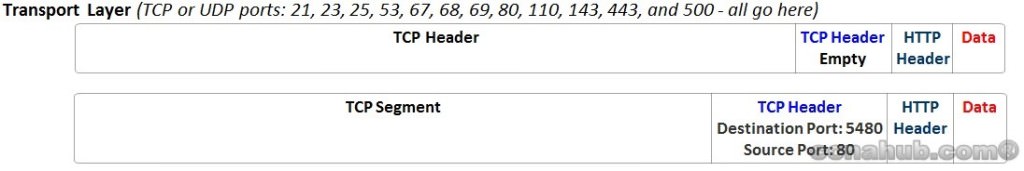
Here where the Data get Segmented based on TCP or UDP Port numbers and IP Addresses, together “IP-Address:Port” called ” TCP Socket or UDP Socket”. The Transport Layer uses the two most common protocols Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP) for Segmenting. This article will mention little bit about TCP Error Recovery. Check Understanding TCP and UDP Protocols Article for More Information.
TCP Error Recovery Overview: uses the concept of Acknowledgments and to appreciate what the TCP does, you must think about the layers above the Transport Layer, starting from Application Layer. Technically, each layer in TCP/IP provides a service to the layer above it, like TCP Error-Recovery service provided especially for Application layer. TCP mechanism guarantee delivery of data across the Network. Therefore, many Application Layer protocols such HTTP requires guarantee data delivery across a network, hence, TCP port 80 is used to recover data segments due to corrupted frames on the way.
Network Layer (3)
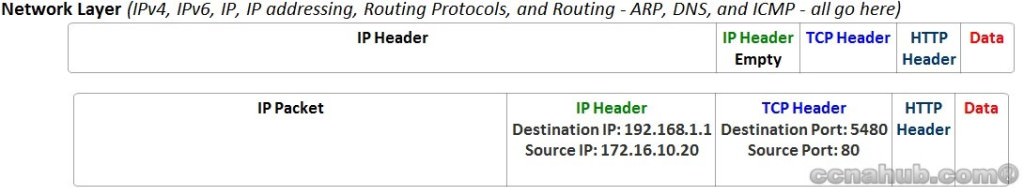
Here where the segments get packaged as IP Packets. Network Layer includes major protocols. Most commonly used: Internet Protocol (IP). IP manage several services like IP Addressing, and IP Routing. This article compares IP Addressing and IP Routing logic concepts with another commonly known concept that uses Addressing and Routing: Postal Service.
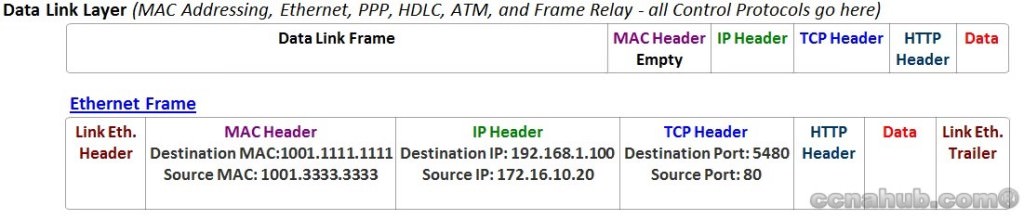
Data-Link Layer (2)
Here where IP Packets get Framed, and here where the last piece of Software control protocol can be applied on the Data before it can be handled as frame to the Hardware Layer (Physical Layer) for bit transmission. Since Data Link Layer has to deal with different media technology, it includes more standards and protocols than Network Layer.
For example, it includes all the variations of Ethernet protocols, along with several other LAN and Wan Technologies. Wide Area Network (WAN) protocol standards which differ significantly compared to Ethernet Standards because of the longer distance involved in transmitting the Data, hence, different type of cable technology used with WAN.
Such WAN Control Protocols are: Point-to-Point (PPP), High-Level Data-Link Control (HDLC), and WAN’s Frame Relay Control Protocols and standards, just to name a few. So in short, Data Link Layer defines the functions used in these Protocols such rules and controls to deliver the IP Packets that hold the data through different types of Physical media.
Physical Layer (1)
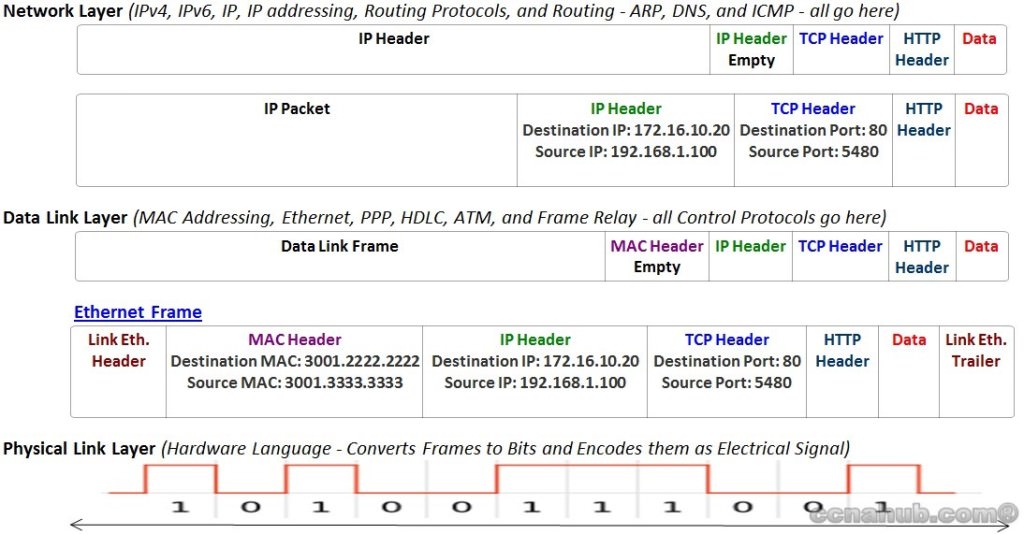
At this stage of the communication process and based on the figures above, the data has been segmented by the Transport Layer using destination and source TCP Port Numbers, placed into an IP packet by Network Layer using a destination and source IP address, and encapsulated as Ethernet Header/Trailer, forming a frame with destination and source MAC addresses.
Next: As Physical Layer on the Downstream and based on the media used, creates an electrical, optical, or radiowave signals that represents the bits in each frame. These signals are then sent on the media one at a time.
It is also the job of the Physical Layer to retrieve those individual signals from the media at the other end’s upstream, restore them to their bit representation, and pass the bits up to the Data Link Layer as a complete frame.
Note: The media does not carry the frame as a single entity. The Media carries signals one at a time to represent the bits that make up the frame. There are three basic forms of network media used to represent the data as signals:
1. Copper Cable – UTP or Coaxial – Electrical Signal
2. Fiber Optic strand – Single Mode or Multi-Mode – Pattern of Light Signal
3. Wireless – Radio Transmission – Radiowave Signal
The representation of the bits – that is the type of signal – so it depends on the type of media. For copper cable media, the signals are patterns of electrical pulses. For fiber, the signals are patterns of light. For wireless media, the signal is patterns of radio wave signal.
E.g. A Host’s Ethernet Interface card or even an Ethernet Switch’s Port combines 2 important hardware functions:
1. The physical layer Control Protocol (Ethernet Control Protocol)
2. And the Encoding and Electrical Signaling Transmitter.
The Network Interface Card or Switch’s Port converts the frame to bits, encodes the bits into electrical signal, and transmits the electrical signals one at a time through the copper cable.
Data Encapsulation overview
Understanding Encapsulation process is very important for Troubleshooting. PC1’s Application Layer encapsulates the contents (GET MSG) inside an HTTP header (1). Then Transport Layer encapsulates the HTTP header and the data inside a TCP header called Segment (2). Then Network Layer encapsulates the TCP Segment inside an IP header called Packet (3). Finally, the Data-Link Layer encapsulates the IP Packet inside Ethernet Link Header and Ethernet Link Trailer called Frame (4), and handled to the Physical Layer for Transmission.
Mapping Encapsulation Process
Person Sending a Letter: The initial step to send a Letter is to “Write a Letter” Application Layer (5) up to Transport Layer (4) act like a Person wrote a letter. These upper layers work the same way regardless of whether the endpoint host or hosts are on the same LAN or are separated by the entire Internet.
To send the letter which is the Data, those upper layers simply handle the letter to the Network layer for packing and delivery procedures. Application Layer and up to Transport Layer are just writers, the lower Layers take the Letter, put it inside an envelope, and choose the best method to deliver it.
So, the Lower Layers starting at Network, Data-link, and Physical layers, act like the Postal Service infrastructure. They stamp, prepare, pack, and deliver messages to the correct destinations.
To do so, those lower layers must understand the underlying physical network because they must choose how to best deliver the data from one host to another. Network, Data-link, and Physical layers together complete the letter or a package delivery process.
The Most Important piece to Route Post Office Letters or IP Packets is: A Solid Addressing System
Internet Protocol (IP) and as part of Network layer, defines that each host should have a different IP address; just as the postal service defines addressing that allows unique addresses for each house, apartment, and business.
IP defines the process of routing so that devices called Routers can work like the Post Office Routing System, Routing Packets of Data so they are delivered to the correct destinations. Just as postal service, created the necessary infrastructure such sorting machines, trucks, planes, and personal to deliver (Route) letters to other individuals that might be located in the same City or located in different City.
Similar work procedure happens at the lower Layers: 3, 2, and 1. The Network Layer defines the details of how a network infrastructure should be managed, so the network can deliver data to all computers in the local Network or to a remote network device using IP Addressing system through IP Routing Procedure.
IP addressing: IP defines addresses for several important reasons. First, each device that uses TCP/IP Model needs a unique address so that it can be identified in the Network. IP also defines how to group addresses together, just like the Postal System groups addresses based on Postal Codes or like Zip codes in the US.
The 32 bit address scheme used by IPv4 called dotted-decimal notation (DDN). E.g. 192.168.1.1. Routers do the equivalent of the work done by each Post office site, therefore, they receive IP packets on various physical interfaces make a decision based on the IP address included with the packet, and then physically forward the packet out on some other network interfaces.
IP Routing: A term used to represent the overall pieces that work together to provide a service of Routing IP packets from any Network device to another. (Like Post Office Mail Routing). Any device with an IP address can connect to the TCP/IP networking model and send packets.
As any one of us can mail using his/her mailing address. Note that even PC/Host still does IP Routing since it is configured with TCP/IP Stack. Computers meant for Data processing and they route among each other if they are located in the same Local Area Network. Routers meant for IP Packet processing and they mainly Route among each other. Finally, Switches meant for Frame Forwarding.
OSI Model – 7 Layers
It is important to mention that many network devices must actually understand the protocols at multiple OSI layers (but in reality all network devices use the TCP/IP Stack), so the layers listed below actually starts with the highest layer that the normal device such PC thinks about when performing its Data Processing Job.
Routers in the other hand, need to think about Layer 3 concepts and must also understand and support features at both Layers 1 and 2.
It’s worth to mention that some Routers act like Firewalls, their filter rules trigger at Layer 7 such Proxy Firewalls and Stateful Firewalls, such routers understand all the way from layer 7 like PC or Server, yet require more horsepower than regular router hardware.
The hardware specs for a Proxy or Stateful firewall would be similar to a Rack Server hardware specs that has more than one CPU and Gigs of RAM.
OSI Layers’ Applications and Protocols
Layer 7 – Application: The application layer is where the protocols and services reside. Examples of Services located here: Telnet, File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP).
Layer 7 provides an interface between the communications software and any application to communicate outside the computer on which the application resides. It also defines the processes for use of authentication.
Layer 6 – Presentation: The presentation layer PRESENTS data to the Application Layer using different presentation data Formats. Examples of Data Formats located here: encryption (like IPSec), ASCII, and JPG.
Layer 6 defines and negotiates presentation data formats such as ASCII text, EBCDIC text, binary, BCD, and jpeg. Encryption defined by the OSI as Presentation Layer data format.
Layer 5 – Session: This layer is responsible for initiating and terminating network connections – Session Manager. Examples of Sessions located here: Remote Procedure Call (RPC) functions and the login portion of a SQL session.
Layer 5 defines how to start, control, and end conversations (called sessions). This includes the control and management of multiple bidirectional messages so that the application can be notified if only some of a series of messages are completed. This allows the upper layer Presentation Layer to have a seamless view of an incoming stream of data.
Layer 4 – Transport: TCP and UDP sockets work at the transport layer. TCP provides reliability, error correction, sequencing, SYN ACK FIN Handshake, and windowing (flow control). Additionally, TCP at the transport layer provides source and destination port numbers that are commonly associated with Servers’ services to form TCP or UDP Sockets.
For example, TCP port 25 is SMTP, 23 is telnet, 22 is SSH, 80 is HTTP, 443 is HTTPS, and so on. These port numbers are very important if you are configuring an Extended ACL. Layer 4 focuses on issues related to data delivery to another computer, such error recovery and flow control.
Layer 3 – Network: The network layer is where the “IP” part of “TCP/IP” happens. IP is responsible for addressing in the network. Because IP works at layer 3, you could also say that routing and routers work at layer 3. Any data at layer 3 is called an IP Packet. Layer 3 defines three main features:
Routing, Logical Addressing, and Path Determination.
1. Routing defines how devices (typically Routers) route IP packets to their final destination.
2. Logical Addressing defines how each device can have an IP address that can be used by the routing process.
3. Path Determination refers to the work done by Routing Protocols to learn possible routes and choose the best route.
Layer 2 – Data Link: If you think of WAN Technologies, there are many protocols that work at layer 2 (like HDLC, PPP and Frame-Relay). However, if you just look at the LAN, the most well-known protocol associated with layer 2 is Ethernet.
The Ethernet protocol uses MAC addresses to identify unique devices on the network. Any data at layer 2 is called a frame. Ethernet switches work at layer 2 to switch Ethernet Frames. To do this, they keep a MAC address table or CAM table – mapping MAC addresses to switch ports.
Layer 2 defines the rules that determine when a device can send data over a particular medium. Data Link Protocols also define the MAC Address and the format of a header and trailer that allows devices attached to the medium to successfully send and receive data (Frames).
Layer 1 – Physical: The physical layer provides the actual connection between devices. Ethernet cables and fiber optic cables work at layer 1. Data goes through the cables via electricity or light. The data at Layer 1 is now represented as bitstream Zeros and Ones.
Layer 1 refers to standards from other organizations. These standards deal with the physical characteristics of the transmission medium, including connectors, pins, use of pins, electrical currents, encoding, light modulation, and the rules for how to activate and deactivate the use of the physical medium.
Easiest way to remember OSI Layers
Most certified professional remember these layers by taking the first letter of the layer and matching it with a word. Here is a common way to remember the OSI model:
“All People Seem To Need Data Processing”
OSI Encapsulation Terminology
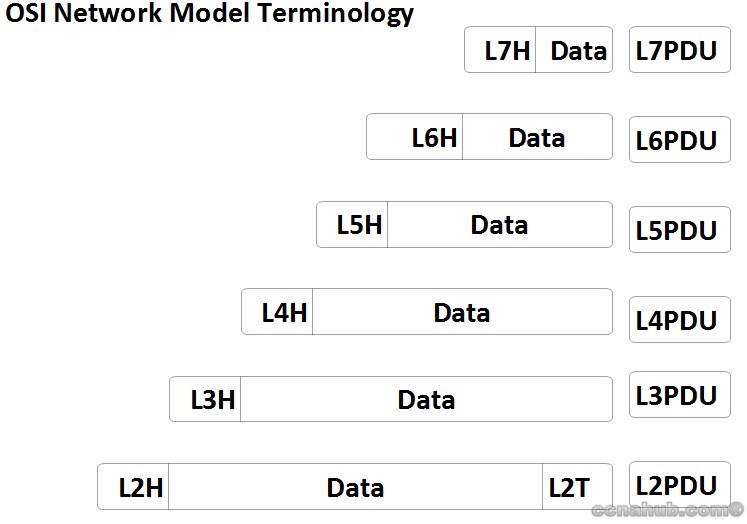
The TCP/IP model uses terms such Segment to refer to Transport Layer, Packet to refer to Network Layer, and Frame to refer to Data-Link Layer.
OSI uses a generic term: Protocol Data Unit (PDU).
Rather than using terms such Segment, Packet, and Frame. OSI simply refers to the layers by PDU as show in the upper figure.
OSI Layers Interaction
Horizontal Layer Interaction: Occurs between the Layers of 2 Computers connected together.
Horizontal Layer Communication or Peer-to-Peer communication, happens when for e.g. Application Layers on 2 computers talk to each other directly. In another word, an Application Layer talks directly to a Remote Host’s Application Layer, each using a specific protocol such HTTP.
E.g. PC1 requested a webpage from a Web-Server using HTTP. After forming a TCP socket and start exchanging data, Peer-to-Peer communication is happening at PC1 using Application layer and at the remote Host (web-server) using the Applications Layer as well.
In another word, any protocol defined by each layer (7 to 1) such http, TCP, OSPF, Ethernet, and so on, uses a header that is transmitted between the computers to communicate what each computer wants to do at either layer 2, 3, 4, or 7.
Any Header added by any Layer’s protocol (7 to 1) of the sending computer such PC1 should be logically processed by the same exact layer of the receiving computer such as Web-Server.
Another E.g. the web-server set a pattern of sequence numbers 1, 2, 3, and so on during a TCP socket data exchange communication session; since both computers using TCP Socket connection, PC1 in this case can determine based on ACK messages if some data did not arrive or a sequence number got lost on the way; PC1 can request the lost data again from the web-server based on a sequence number ( which it’s a TCP Error Recovery Feature).
This process through which two computers set and interpret the information in the header used by Transport Layer is called Horizontal Layer Interactions, and it occurs between 2 computers that are communicating over a network using the same layer functions.
Vertical layer Interaction: Occurs on the same Computer – Layer 7 to 1 or Layer 1 to 7.
Vertical layer Communication, happens on a single computer, one layer provides a service to a higher layer. The software or hardware that implements the higher layer requests that the next lower layer perform the needed functions.
E.g. the higher layer protocol such HTTP informed the Transport layer that it needs an error recovery since some web data got corrupted. Transport Layer with TCP providing Error Recovery service, informed the Remote Host and requested the lost data again based on sequence number, once the data re-transmitted again from the remote host and received by the Transport Layer, it handles the data again to the Application Layer HTTP.
This communication between the Application Layer straight down asking the Transport layer for TCP Error Recover Feature and waiting for respond is called Vertical Layer Interaction.
Finally, Prepare for Certification and for the Real World
Certainly, any entry-level certification will require you to learn about TCP/IP and OSI models and answer some questions about it. ICND1 certification requires that you understand the TCP/IP and OSI models. I believe this all comes back again to knowing How Important to understand TCP/IP and OSI Models.
Once you Understand and become familiar with TCP/IP and OSI models Concept, you will be Professional in IP Network Design, Build, and Troubleshoot.
Subject Related
By W3 Schools | Inet Daemon | HighTech | TCP/IP Guide | Penguin Tutor | Tutorials Points | IP Fundamentals | Introduction To Network | TCP IP Dummies | TCP IP Foundation | TCP/IP Protocol Suite | Teach Yourself TCP/IP | Internet working TCP/IP | TCP Guide Comprehensive
CCNA Routing and Switching
<< IP and Network Fundamentals Course
>> Models, Protocols, and Standards Section
- Understanding TCP/IP and OSI Models
- Understanding Packet Flow Across the Network Part1
- Understanding Packet Flow Across the Network Part2
- Understanding Ethernet LAN Standards
- Understanding Ethernet MAC Addresses
- Understanding WAN Technologies
- Understanding Data Link Layer Encapsulation
- Understanding EoMPLS WAN Technology
- Understanding IP Routing Process Concept
- Understanding Web Browser DNS Lookup
- Understanding ARP Broadcast Message
- Understanding TCP and UDP Protocols
- Understanding TCP and UDP Multiplexing
- Understanding Application Layer Services
- Understanding Quality of Service Concept



Very Nice Article. Notes will definitely help with my exam. Thank you!
Sorry Daniel for being late. I am glad that you found this article helpful and good luck with the exam 🙂
Very nicely explained Imad, very helpful.
This is great information. I came across this website looking for good material that would help my pass the CCNA exam and this looks outstanding. I like how your topics questions relate to the study guide questions on the Cisco website. Thanks!
You are Welcome Daniel. That was actually one of the main things I focused on, is to relate each article to its Exam topics. I really appreciate your comments and thank you for sharing your thoughts.
Good explanation of the topic, thanks!
Thank you so much Wesley for your feedback, please share the knowledge.