Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Post Linux OS Setup Initial Steps Section
- Understanding Root Account Privileges Methods
- Creating and Adding Local Users to Sudoers List
- Installing Linux Virtual Machine Guest Additions
- Cloning Virtual Machines using VM Snapshot

Creating and Adding Local Users to Sudoers List is highly crucial to master. Having said this, I will show you how to create and add Admin users to admin list called sudo Members List. Since the rest of the courses will be heavily based on such skills and fundamentals, it’s highly recommended to take your time and master the user and groups management side, especially when you need later on to add or remove Admin users from your Linux system.
Objectives:
1. Creating Local Users for Admin Purpose
2. Debian Base – Adding Local Users to Sudoers
3. Red Hat Base – Adding Local Users to Sudoers
Prerequisites:
A. Basic Debian or Red Hat Base System Knowledge
B. Login as Root or use a User with Root Privilege
C. Login to your DigitalOcean or Vultr Account
Table of Contents
Creating Local Users for Admin Purpose
I usually create one or two users and assign them to sudoers list or sudo group. To assign users to sudo members list, you need to create users in the first place using adduser script or use Linux/UNIX native commands.
Using adduser script
TIP: If adduser script not available, use the Linux Native commands instead as shown below.
a. Debian Base Systems
adduser imad
You would see such progress…
root@node1:~# adduser imad
Adding user `imad' ...
Adding new group `imad' (1001) ...
Adding new user `imad' (1001) with group `imad' ...
Creating home directory `/home/imad' ...
Copying files from `/etc/skel' ...
Enter new UNIX password:
Retype new UNIX password:
passwd: password updated successfully
Changing the user information for imad
Enter the new value, or press ENTER for the default
Full Name []: Imad Daou
Room Number []: 347
Work Phone []: 347-555-5555
Home Phone []: 718-555-5555
Other []:
Is the information correct? [Y/n] y
root@node1:~#
Note: when you create a Linux user, adduser script command creates a group as well which carries the same name of the user.
b. Red Hat Base Systems
Run the following steps ( 1 to 2)
1. Using adduser Command
adduser imad
2. Unlock the user by Setting a Password
passwd imad
Changing password for user imad. New password: Retype new password: passwd: all authentication tokens updated successfully. [root@node1 ~]#
Using Linux/UNIX Native Commands
In case the adduser command not available, use the following commands:
Run the following steps ( 1 to 3)
1. Create Linux/UNIX Group
groupadd linuxadmin
2. Create linuxadmin User
useradd -m -g linuxadmin -s /bin/bash linuxadmin
3. Set a Password for linuxadmin User
passwd linuxadmin
Debian Base – Adding Local Users to Sudoers
Sudoers can run configuration commands using sudo before each command from their session without using root user or su command. Besides, it’s easy to add and remove users from sudoers’ member list.
Run the following steps ( 1 to 7)
1. As root Install sudo Package
apt-get update && apt-get install nano
2. Install Group Listing Package
apt-get install members
List Available Users
awk -F':' '{ print $1}' /etc/passwd
TIP: If you are using private virtualization platform such VirtualBox instead of Public VPS, then you should see the user you have created during OS setup.
List Available Groups
awk -F':' '{ print $1}' /etc/group
You should see the group which belong to the user you have created during OS setup. E.g. imad user will be associated with imad group.
List a specific group
Of course, replace imad with your group.
awk -F':' '{ print $1}' /etc/group | grep imad
List the Members of this group
members imad
3. Adding Users to Sudoers List
2 known options to add users to Sudoers list.
a. Add users individually to sudoers file
Or
b. Add users to sudo group
I will show you both ways:
4. Using option a by editing sudoers file
nano /etc/sudoers
Scroll down to “User privileges specification” and add users as shown:
# User privileges specification
root ALL=(ALL:ALL) ALL
imad ALL=(ALL:ALL) ALL
linuxadmin ALL=(ALL:ALL) ALL
Save: Ctrl-X, Hit Y Key, and Enter.
5. Test it. login as linuxadmin User
Open new putty window:
Or from root session
root@node1:~# login linuxadmin
Then run apt-get Command using sudo
sudo apt-get update
Enter Linuxadmin user password:
You might face the following message…
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for linuxadmin:
After entering linuxadmin’s password, updating apt-get cache should start as shown below:
Hit http://ftp.us.debian.org wheezy Release.gpg Hit http://ftp.us.debian.org wheezy-updates Release.gpg Hit http://ftp.us.debian.org wheezy Release Hit http://ftp.us.debian.org wheezy-updates Release Hit http://ftp.us.debian.org wheezy/main Sources Hit http://security.debian.org wheezy/updates Release.gpg Hit http://ftp.us.debian.org wheezy/main amd64 Packages Hit http://security.debian.org wheezy/updates Release Hit http://ftp.us.debian.org wheezy/main Translation-en Hit http://ftp.us.debian.org wheezy-updates/main Sources Hit http://ftp.us.debian.org wheezy-updates/main amd64 Packages/DiffIndex Hit http://security.debian.org wheezy/updates/main Sources Hit http://ftp.us.debian.org wheezy-updates/main Translation-en/DiffIndex Hit http://security.debian.org wheezy/updates/main amd64 Packages Hit http://security.debian.org wheezy/updates/main Translation-en Reading package lists... Done linuxadmin@node1:~$
Type Exit to Logout from linuxadmin
As you can see, my admin user “linuxadmin” was able to run configuration commands such apt-get update using sudo before the command. Advantages of Sudo Members are: 1) Admin accounts don’t need root password to run configuration commands, 2) any member can be easily removed from the list.
6. Using option b by adding users to sudo group
Sudo group is part of sudo list, any user that is part of sudo can run configuration commands, however, you need to disable the users from using sudoers file by using hash sign as shown below.
nano /etc/sudoers
Scroll down to “User privileges specification”
# User privileges specification root ALL=(ALL:ALL) ALL #imad ALL=(ALL:ALL) ALL #linuxadmin ALL=(ALL:ALL) ALL
Save: Ctrl-X, Hit Y Key, and Enter.
Adding imad user to sudo Group
adduser imad sudo
root@node1:~# adduser imad sudo Adding user `imad' to group `sudo' ... Adding user imad to group sudo Done.
Adding linuxadmin user to sudo Group
adduser linuxadmin sudo
root@node1:~# adduser linuxadmin sudo Adding user `linuxadmin' to group `sudo' ... Adding user linuxadmin to group sudo Done.
7. List Sudo Group Members
members sudo
Remove users from sudo group
deluser imad sudo
root@node1:~# deluser imad sudo Removing user `imad' from group `sudo' ... Done.
Run members command again to confirm removing
members sudo
Now, if imad tried to run configuration command, he will be prompted by the following message:
imad@node1:~$ sudo apt-get update
[sudo] password for imad:
imad is not in the sudoers file.
This incident will be reported.
imad@node1:~$
Finally, if you want to delete the user totally from the system:
deluser --remove-home imad
root@node1:~# deluser --remove-home imad Looking for files to backup/remove ... Removing files ... Removing user `imad' ... Warning: group `imad' has no more members. Done.
Note: that imad group has been deleted as well.
Confirm User deletion
awk -F':' '{ print $1}' /etc/passwd | grep imad
Should return nothing
And
awk -F':' '{ print $1}' /etc/group | grep imad
Should return nothing as well.
Remember: By adding users to sudoers file or sudo group, users will be given admin privilege, hence, they can run configuration commands using sudo before each command. Which way is better to use: sudoers file or sudo group? I believe adding users to sudo group is better, however, you should know both ways. Finally, you need to create users before adding them as sudoers.
Red Hat Base – Adding Local Users to Sudoers
Sudoers can run configuration commands using sudo before each command from their session without using root user or su command. Besides, it’s easy to add and remove users from sudoers’ member list.
Run the following steps ( 1 to 6)
1. Install Required Packages
yum install sudo nano members
List Available Users
awk -F':' '{ print $1}' /etc/passwd
TIP: If you are using private virtualization platform such VirtualBox instead of Public VPS, then you should see the user you have created during OS setup.
List Available Groups
awk -F':' '{ print $1}' /etc/group
You should see the group which belong to the user you have created during OS setup. E.g. imad user will be associated with imad group.
List a specific group
Of course, replace imad with your group.
awk -F':' '{ print $1}' /etc/group | grep imad
List the Members of this group
members imad
2. Adding Users to Sudoers List
2 known options to add users Sudoers list.
a. Add users individually to sudoers file
Or
b. Add users to wheel group
I will show you both ways:
3. Using option a by editing sudoers file
nano /etc/sudoers
Scroll down to the following, add users as needed and save.
## Allow root to run any commands anywhere
root ALL=(ALL) ALL
imad ALL=(ALL) ALL
linuxadmin ALL=(ALL) ALL
Save: Ctrl-X, Hit Y Key, and Enter.
4. Test it. login as linuxadmin User
Open new putty window:
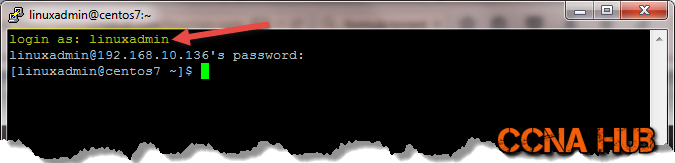 Or, from root, use su with dash to switch to another user:
Or, from root, use su with dash to switch to another user:
su - linuxadmin
Then run yum Command using sudo
sudo yum update
Enter Linuxadmin user password:
We trust you have received the usual lecture from the local System
Administrator. It usually boils down to these three things:
#1) Respect the privacy of others.
#2) Think before you type.
#3) With great power comes great responsibility.
[sudo] password for linuxadmin:
After entering linuxadmin’s password, yum update should start as shown below:
Loaded plugins: fastestmirror, priorities Setting up Update Process Loading mirror speeds from cached hostfile * base: mirror.rackspace.com * epel: ftp.osuosl.org * extras: mirrors.greenmountainaccess.net * remi: rpms.remirepo.net * remi-safe: rpms.remirepo.net * rpmforge: repoforge.mirror.constant.com * updates: mirror.symnds.com 1740 packages excluded due to repository priority protections No Packages marked for Update linuxadmin@centos6:~$
Type Exit to Logout from linuxadmin
As you can see, my admin user “linuxadmin” was able to run configuration commands such yum update using sudo before the command. Advantages of Sudo Members are: 1) Admin accounts don’t need root password to run configuration commands, 2) any member can be easily removed from the list.
5. Using option b by adding users to wheel group
Wheel group is part of sudo list, any user that is part of wheel can run configuration commands. However, you need to disable the users from using sudoers file by using hash sign as shown below, and enable the wheel group by removing the hash sign.
nano /etc/sudoers
Scroll down to the following:
## Allow root to run any commands anywhere root ALL=(ALL) ALL #imad ALL=(ALL) ALL #linuxadmin ALL=(ALL) ALL
## Allows people in group wheel to run all commands
%wheel ALL=(ALL) ALL
Save: Ctrl-X, Hit Y Key, and Enter.
Adding imad user to wheel Group
gpasswd -a imad wheel
Adding linuxadmin user to wheel Group
gpasswd -a linuxadmin wheel
6. List Wheel Group Members
members wheel
Or for CentOS7
lid -g wheel
Remove users from wheel group
gpasswd -d imad wheel
Run members command again to confirm the remove
members wheel
Or for CentOS7
lid -g wheel
Only linuxadmin should be inside wheel group. If imad tried to run configuration command, he will be prompted by the following message:
imad is not in the sudoers file.
This incident will be reported.
Finally, if you want to delete the user totally from the system:
userdel -r imad
Note: that imad group has been deleted as well.
Confirm User deletion
awk -F':' '{ print $1}' /etc/passwd | grep imad
Should return nothing
And
awk -F':' '{ print $1}' /etc/group | grep imad
Should return nothing as well.
Remember: By adding users to sudoers file or sudo group, users will be given admin privilege, hence, they can run configuration commands using sudo before each command. Which way is better to use: sudoers file or sudo group? I believe adding users to sudo group is better, however, you should know both ways. Finally, you need to create users before adding them as sudoers.
Subject Related
By | Debian Help | Ubuntu Docs | Red Hat Docs | CentOS Docs
Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Post Linux OS Setup Initial Steps Section
- Understanding Root Account Privileges Methods
- Creating and Adding Local Users to Sudoers List
- Installing Linux Virtual Machine Guest Additions
- Cloning Virtual Machines using VM Snapshot

LEAVE A COMMENT