Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Post Linux OS Setup Initial Steps Section
- Understanding Root Account Privileges Methods
- Creating and Adding Local Users to Sudoers List
- Installing Linux Virtual Machine Guest Additions
- Cloning Virtual Machines using VM Snapshot

In order to implement configuration articles, I need root privileges access. Understanding Root Account Privileges Methods will prepare you with 3 different methods to gain root privileges when you need to configure your Linux system. It is crucial to understand all methods of root account privileges access, and the difference among them before start configuring your Linux VM or VPS.
Objectives:
1. Understanding Root Privileges Methods
2. Setting or Changing Root Account Password
3. Allowing Root Login through SSH Sessions
4. Using su to Run Configuration Command
Prerequisites:
A. Basic Debian or Red Hat Base System Knowledge
B. Debian or Red Hat Base Minimal Server Setup
C. Login to your DigitalOcean or Vultr Account
Note: Using VPS provider such DigitalOcean or Vultr, you don’t need to worry about setting up the OS, besides, the root account password will be emailed you to as well. Meaning, root account can be used out of the box. However, I recommend using SSH-Keys when using a Public VPS.
Table of Contents
Understanding Root Privileges Methods
You need Root privileges to run configuration commands. Security professionals recommend to be familiar with all root access methods for too many reasons. For example, In-house Admins and Owners should be familiar with all 3 methods in case they need to higher or grant outside Professional access to work on their system. So, there are 3 root access methods to gain superuser privileges in order to run configuration commands:
Method A: Login Directly Using root Account
To Login directly as root. Method A is straight forward, continue logged in as root to finish all configuration articles, and once you done, you can disable SSH root login if you want to. (I recommend to use this method A to implement all configuration articles)
Method B: Login as Regular user and Switch to root using su Command
Login as regular user, and switch to root session using su command. However, this method requires that other users should know root password if root password has been set. (As owner or SysAdmin you would know or has set the root password, however, you shouldn’t share your root password with other users, and that’s where Method C comes into play)
Note: you can run configuration commands as root using su command, once you done, exit root session. The disadvantage of Method B, that other users must know root password to manage the system, which is not suitable choice if you need to hire outside professionals or ask a friend for help.
Method C: Elevate to root Privileges using sudo before each command
However, the user who should use sudo must be part of sudo list. Any user that is part of Sudoers members can use sudo command before any configuration command to configure the system. But, method C requires that you install sudo package if not already installed. (This method is suitable to Admin users which are NOT suppose to know root password, and it’s the preferred way for Daily Maintenance Admins or third party Admins when they need access to the system.)
Who are Sudoers? They got limited root privileges but enough to manage the system. Adding users to sudoers list, will allow owners or Sysadmins to give limited root privileges to other users and log their root activities. The basic philosophy is to give as few privileges as possible but still allow other users to configure or maintain the system and get their work done.
Which Method you should use? As owner: 1) I will use method A to implement all the initial configuration required, 2) I can disable ssh root login when I am done from initial configuration stage. 3) After my Web Hosting Server is up and running, I will use method C for daily maintenance.
My personal preference: I like to accomplish all initial configuration stage across all courses using root account due to No restriction, however, I can disable SSH for root account when I finish the initial configuration. After the system is up and running, I will use Sudo member user for daily admin use instead. Optional, when it comes to Public VPS, I don’t disable SSH access for root if 1) SSH Password Authentication disabled, 2) I am using SSH-Keys authentication instead of SSH Password Authentication.
Setting or Changing Root Account Password
a. Debian Base Systems
During Debian OS setup, the system allows you 1) to set a root account password, 2) to create a regular account, however, it won’t add the regular account you created to Sudoers List (Admin Users).
Ubuntu in the other hand, won’t allow you to set a root account password during OS setup, however, it adds the regular user you created during OS setup to Sudoers List. So, after Debian OS setup is done (Or VPS has been created), I can use root account right away, but after Ubuntu OS setup is done (and not necessarily after VPS creation) you have to login as regular user and use sudo to elevate to root privilege.
TIP: Most VPS providers enable root account for you to use out of the box.
b. Red Hat Base Systems
During CentOS OS setup, the system allows you to set root account password, and the latest version should allow you to create regular users and add them to an Admin group (wheel sudoers group) as well.
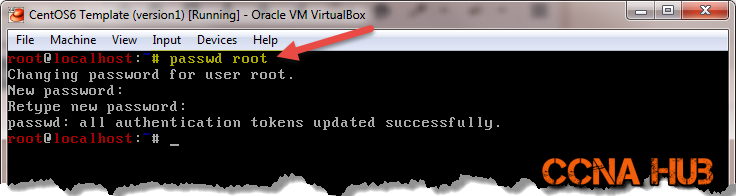
Set or Change root account password
Works on any Linux distribution. If you like to change the root password, or simply set a more complex root passphrase, run the following command from the Terminal Window as shown below:
passwd root
If you use Ubuntu, use sudo before the command.
sudo passwd root
Using either VirtualBox, VMware Terminal Window, or even the VPS Web Console, type passwd root:
Allowing Root Login through SSH Sessions
TIP: VPS providers enable SSH root login by default, as a mater of fact, it’s recommended to disable it once you done from setting up your Web Hosting Solution. But, you need the following procedure to enable SSH root login if you are setting up your WHS on private Virtualization environment.
You probably don’t need these steps at Red Hat Base Systems, however, starting from Debian8 system, root account was denied access using SSH sessions. But it’s easy to enable it using one of the following 3 options:
A. Edit sshd_config straight on the terminal Console window.
B. SSH first to the Server using the account you created while you were setting up the Server OS, use su command to enter root session, then edit the sshd_config file to allow ssh for root.
C. Login using a sudoer member, however, using Debian for example, the created regular user during OS setup won’t be sudoer member, therefore, you are left with option a and b. Using Ubuntu or CentOS, the created user during OS setup can be part of sudoers, hence, you can use option C.
Note: When I mention Terminal, I mean you are logging in straight at Linux machine. This machine could be physical VirtualBox, VMware Station, or Proxmox Machine Terminal window, meaning, no SSH is being used and you are right on the console. In terms of a VPS, Web Console is equal to a Terminal Window.
Option A: suitable if you can login from the Terminal as root after OS Setup
Run the following steps ( 1 to 2) at the Terminal
First, I would make sure if nano editor is installed. If you use vi or vim, I recommend using nano instead.
Debian Base
apt-get nano install
Red Hat Base
yum nano install
1. Edit sshd_config file
nano /etc/ssh/sshd_config
Scroll or search using Ctrl-w for Authentication filed:
Under PermitRootLogin
It could be “PermitRootLogin prohibit-password” or “PermitRootLogin without-password”
Change it From:
# Authentication:
[...]
PermitRootLogin without-password
[...]
To:
# Authentication:
[...]
PermitRootLogin yes
[...]
Save: Ctrl-X, Hit Y Key, and Enter.
2. Restart sshd Services
service sshd restart
Now, you can use Putty to SSH using root account.
Option B: suitable if you can’t login as root from Terminal after OS Setup
Run the following steps ( 1 to 7) using ssh client
Using the account you created during OS setup, login and use su command in order to enable ssh session for root account.
1. View IP Address from the Terminal Window
ifconfig
Or
ip addr
2. Fire up ssh client such Putty
Type the IP address you viewed by ifconfig command in Putty and connect.
3. Login Using Local User Account
4. Switch to root Session Using su Command
Note: Make sure you know or have set a new root password.
su
Enter root password to continue…
imad@node1:~$ su Password: root@node1:/home/imad#
5. Now, Edit sshd_config file
Now, you are at the root session, edit the file.
nano /etc/ssh/sshd_config
Scroll or search using Ctrl-w for Authentication filed:
Under PermitRootLogin
It could be “PermitRootLogin prohibit-password” or “PermitRootLogin without-password”
Change it From:
# Authentication:
[...]
PermitRootLogin without-password
[...]
To:
# Authentication:
[...]
PermitRootLogin yes
[...]
Save: Ctrl-X, Hit Y Key, and Enter.
6. Restart sshd Services
service sshd restart
7. Type exit to Exit root Session
root@node1:/home/imad# exit exit imad@node1:~$
Now, try to SSH again using root instead of regular user. You should be able to login as root.
Use su to Run Configuration Commands
TIP: As owner, only needed if you there is no way for you to Login or SSH using root account.
Run the following steps ( 1 to 3)
1. First, login using the regular user.
Note: Either Debian or Red Hat Base systems, su command should carry the same functions:
2. Switch to root Session Using su Command
su
Enter root password to continue…
[imad@node1 ~]$ su Password: [root@node1 imad]#
3. Type exit to Exit root Session
[imad@node1 ~]$ su Password: [root@node1 imad]# exit exit [imad@node1 ~]$
Note: You can use su command to run configuration commands. Again, if you need help from friend or third party professionals, then sharing root password is not recommended option. Instead, create a regular user for that purpose such linuxadmin, add it to sudo members, then give this user to a friend or professional support. Leave su command only for yourself. Next, I will show you how to create Local Admin accounts and add them to Sudo Members List.
Subject Related
By Wikipedia Superuser | Root Account | Linux Acedamy – Sudo Usage
Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Post Linux OS Setup Initial Steps Section
- Understanding Root Account Privileges Methods
- Creating and Adding Local Users to Sudoers List
- Installing Linux Virtual Machine Guest Additions
- Cloning Virtual Machines using VM Snapshot


LEAVE A COMMENT