Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Configuring SSH-Key Based Authentication Section
- Understanding SSH-Keys Based Authentication
- Creating SSH-Keys using Putty Keys Generator
- Creating Public VPS Droplet using DigitalOcean
- Managing Linux VPS Instance via Putty SSH Client
- Managing Linux VPS Instance via WinSCP Client
- Creating SSH-Keys using Terminal Keys Generator
- Switching SSH Password to SSH-Keys Authentication
- Uploading Admins and Friends SSH-Keys to VPS
- Uploading SSH Public Keys using VPS Panel
- SSH Hopping using SSH Agent Forwarding
- Deploying Public VPS instance using Vultr Provider
- Securing and Hardening SSH Server Configuration
- SSH Server and Client Most Known Error Messages

Uploading Admins and Friends SSH-Keys to your VPS could be handy if one day 1) You have leased a VPS but the control panel doesn’t provide you creating VPS using SSH-Keys, 2) you need help fixing or configuring your Server, hence, you can ask a professional person or friend for Help. Finally, your VPS should accept ONLY SSH-Keys Authentication and refuse SSH Password Authentication.
Objectives:
1. Understanding the Purpose Behind Adding Others Public Key
2. Assigning an Admin Account for One of Your Friends
3. As SysAdmin – Copy/Paste your Friend’s Public Key
4. As Friend – SSH to the VPS Using the Admin Account
Prerequisites:
A. Basic Debian or Red Hat Linux Knowledge
B. Login to your DigitalOcean or Vultr Account
TIP: You can always create more than one Admin account, one for your personal use such Daily Maintenance, and another account for outside support team. Hence, you can upload SSH-Keys for your own use as well.
Table of Contents
Understanding the Purpose Behind Adding Others Public Key
Let’s assume one day you need help configuring or troubleshooting your system, and the professional person is your friend or trusted Professional you know. In order for anyone to connect and work on your VPS, you have first to ask your friend for his/her Public Key.
Once you receive his/her Public key, you can copy/paste it or upload it to the Admin account’s authorized_keys file, (This Admin account is intended for outside support and should be part of sudo Member List), therefore, your friend can access your VPS using this Admin account and Authenticate to your VPS using his/her SSH-Keys.
As you probably know, there is NO similar SSH-Keys pair around the world, and uploading someone’s Public Key to your VPS (Such your friend’s Public Key), will assure you 100% that this person is really your friend and not someone else.
Security Note: Nevertheless, there are rare cases where if your friend doesn’t secure his/her laptop properly against Spyware and Trojans, then any Cracker can sniff his/her Private key and its Passphrase. In this situation, you won’t be sure who is Authenticating to your System.
I always recommend to confirm security measures with your friends before uploading their Public Key. Admin Station’s Security Measures should be such keeping the laptop up2date with OS, Antivirus, and Anti-spyware updates, besides, have a Firewall and Intrusion Detection such K9-Bluecoat for Windows or MAC is a must before considering this station as Remote Management Station.
Let’s assume you work for a company, they will assign you an Admin account to manage their Systems or their customer’s systems, and when your manager ask you to support one of the systems, he would have uploaded your company’s laptop Public Key to the intended VPS before you try to SSH.
Most companies assign laptops to their professionals that is highly secure and monitored to assure authenticity, or have you Remote Desktop to their terminal Services and from there access their Linux/UNIX systems. Why such security measurements? because they want to make sure that you are the one who is authenticating and not someone else.
Let’s start, below I will show you the scenario where you needed help from a friend and you have asked him/her to send you the Public key first before he or she can access your VPS.
Note: I have mentioned previously that your VPS eventually must accept only and only SSH-Keys Authentication, and SSH Password Authentication must be disabled. When you disable SSH Password Authentication later on using Secure and Harden SSH Server Configuration article, your VPS won’t accept SSH Password Authentication logins anymore.
Which means, no one in this world can access your VPS unless you upload their Public Key, therefore, it’s important to understand that your friend’s SSH-Keys is the only way for him or her to Authenticate to your VPS and Not the Admin’s account Password.
Besides, please remember that SSH-Keys was not meant to cancel out all type of Password Authentication from all type of interfaces such Web Console or Physical Terminal. Disabling SSH Password Authentication doesn’t Disable Web Console Password Authentication.
Which means, you can still login to your VPS using Password Authenticate from the Web Console, but not from the SSH client such Putty or Linux/UNIX ssh-client, which makes it impossible for Intruders to penetrate your system using SSH sessions. Why? They got to have a copy of your Private Key and the Passphrase to login, and that is the beauty of SSH-Keys!
Disabling SSH Password Authentication is a must step after you setup and test SSH-Keys Authentication. There will be no advantage or any use of SSH-keys if you still allow SSH sign in using Password Authentication.
Assigning an Admin Account for One of Your Friends
As Sysadmin: you should have already created an Admin account such linuxadmin user as shown in previous articles and added this user to sudo members list.
As Friend: you should have created your SSH-keys using either Putty or Linux/UNIX ssh-client and sent the Public Key to the SysAdmin for upload.
As SysAdmin: you should have received your friend’s Public Key by email, and he/she is waiting for your reply. Your friend would need from you to email 5 things:
1. that you have uploaded his/her public key under the Admin account’s authorized_keys file. E.g. if linuxadmin user would be used, then upload it to linuxadmin’s authorized_keys file.
2. VPS IP Address or sub-domain should be used to connect.
3. The first and the Last 2 digits of Server’s ECDSA and RSA Fingerprints in order to verify the server’s key fingerprint before authenticating.
4. The Admin account should be used during SSH connection e.g. linuxadmin user.
5. The Admin’s account password should be used to manage the system. Notice, that your friend will ssh and login using his/her SSH-Keys since you uploaded his/her Public Key, but when it comes to manage your system, the Admin user’s password will be used.
The Admin’s account password in this case would be used Only and Only to manage the system and not to authenticate during SSH. The moment your friend uses sudo command before any configuration command will prompt him/her to enter that Admin’s account password, hence, the admin’s account password won’t be used for SSH Authentication, rather, is only used to unlock root privilege so your friend can run configuration commands.
As Friend: Based on where you have created your SSH-Keys, you can use Putty or Linux/UNIX ssh-client to login to the VPS once you receive the email confirmation from the SysAdmin, which should include:
1. VPS IP Address or sub-domain should be used to connect.
2. Server’s Key fingerprints of ECDSA and RSA to verify the Server before clicking or Typing Yes during connection.
3. The Admin account should be used during SSH Authentication.
4. The Admin’s account password to manage the system when sudo is used.
As SysAdmin – Copy/Paste Your Friend’s Public Key
Once you receive your friend’s Public Key, copy and paste that Public Key under the Admin’s account authorized_keys file.
Run the following steps ( 1 to 8)
Note: replace linuxadmin user using your user.
First SSH as root, then from root session login as linuxadmin user as shown below.
1. From root Session, login to linuxadmin User
Debian based
login linuxadmin
CentOS based
su - linuxadmin
Note: When you login as other user such linuxadmin that has been part of sudoers, run a command such apt-get update (Debian) or yum update (CentOS) to unlock its root privileges.
2. Run apt-get update Command
Debian based
sudo apt-get update
CentOS based
sudo yum update
Once you run sudo command, you will be prompted by the following message to enter linuxadmin’s password in order to unlock its root privileges:
Note: of course you are using different user.
We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. [sudo] password for linuxadmin:
Enter linuxadmin’s password to continue.
Next, from linuxadmin’s session, let’s prepare linuxadmin’s SSH environment to add your friend’s Public Key to linuxadmin’s authorized_keys file.
3. Create .ssh Directory Under linuxadmin
sudo mkdir $HOME/.ssh
4. Change Directory Permission
sudo chmod 700 $HOME/.ssh
5. Create authorized_keys File
Note: All linuxadmin’s Public keys will be saved under one single file – authorized_keys. Each Public Key should be on its line. It’s worth to mention, that if your friend own Windows and Linux/UNIX stations, he or she can later on upload more than public key to access your VPS from different stations.
sudo touch $HOME/.ssh/authorized_keys
6. Change authorized_keys Permission
sudo chmod 600 $HOME/.ssh/authorized_keys
7. Make Sure linuxadmin is the Owner
sudo chown linuxadmin:linuxadmin -R $HOME/.ssh
8. Now, Add Your Friend’s First Public Key
sudo nano $HOME/.ssh/authorized_keys
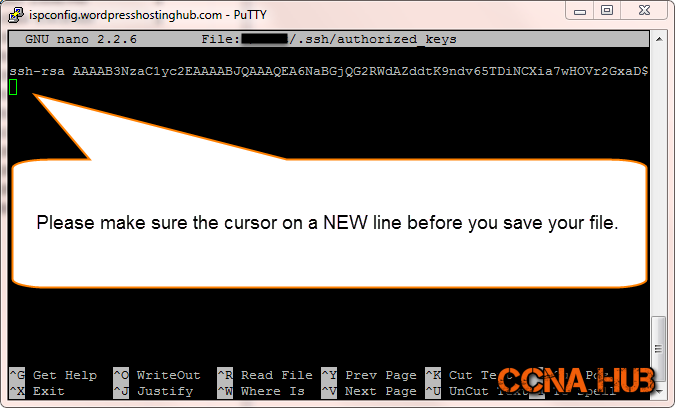
Very Important: Make sure you hit Enter at the end of the Public Key after you paste the public key inside the authorized_keys file, the cursor should be on a new line before you save the file as shown in the image below.
Save: Ctrl-X, Hit Y Key, and Enter.
As Friend – SSH to the VPS Using the Admin Account
Note: This account can be your personal account as well, in case your dealing with a VPS that was created without SSH-Keys.
SSH to the VPS using the station where you have created your Public Key, verify the Server’s Key fingerprint, and login using the Admin account that you have received from the SysAdmin. Use the Admin account’s password when you use sudo command. For more information about how to use Putty or Command Line, please refer to SSH to Your VPS Using Different SSH Clients Part1 and Part2 articles.
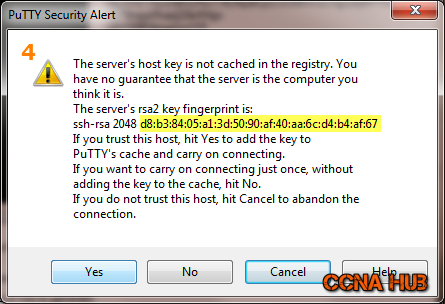
Assuming you have created your Public Key using Putty on Windows, in your first attempt, you should see the Putty Security Alert message as shown below. Note that Putty supports only RSA fingerprints. This an example fingerprint, the VPS you are trying to access, should have different fingerprint. Based on the SysAdmin email, verify the first and the last 2 digits of RSA fingerprint, then click Yes to continue.
How about Uploading Extra Public Keys?
If you have used putty to create your first Public Key, and you have logged in to the VPS successfully using Putty, then you can upload a 2nd Public Key that belongs to different Windows or Linux/UNIX station, or simply vise versa. If you have created your first Public Key using Linux/UNIX station, then you can upload a Putty’s Public key as well to access the VPS from Windows Station. It’s very simple though, follow the steps below to upload a 2nd Public Key that belongs to either Putty or Linux/UNIX Station.
Uploading Using Putty from Windows
First, you should have created SSH-Keys at your 2nd station, this station can be Windows or Linux/UNIX station, copied and paste the Public Key to a text file that is accessible by the first Station or simply copy it to usb stick. As an alternative, you can send it email to your self, or use dropbox between the 2 stations.
Remember, the Admin’s account Authorized_keys file can carry all your Public Keys from different stations (the SysAdmin already has added your first Public Key). Meaning, if you use Putty and you need to add another Public Key, just append it to the existence Public Key, each key must be on its line.
To upload extra Public key that belongs to different station is straight forward. All you have to do is edit the VPS authorized_keys file at the VPS and Copy/Paste the New Public Key.
Edit the VPS Authorized_keys File
nano $HOME/.ssh/authorized_keys
You will find that the SysAdmin has added your first Public Key, right under neath that key on NEW Line, Paste your second Public Key which can be for another Windows or Linux/UNIX station.
Very Important: At the end of the pasted New public key, press enter to see your courser moved to a new line, then save the file.
Save: Ctrl-X, Hit Y Key, and Enter.
Uploading Using Terminal from Linux/UNIX
Again, the 2nd public key could belong to Putty or simply another Linux/UNIX station. Just remember, when you create your SSH-Keys, specifying a comment will help you locate where the Public Key has been created and to whom it belongs.
Method1 – Using ssh-copy-id command
Note: ssh-copy-id command requires OpenSSH package. Below, replace linuxadmin user using the Admin account you suppose to use, specify the 2nd public key’s path location, and replace VPS-IP-ADDRESS using the VPS IP Address should be used. -i switch will be used to specify public key’s path location.
ssh-copy-id command will make sure that the 2nd Public Key will be appended to linuxadmin’s authorized_keys file on a New line beside the Public Keys that are already there. The last thing you need is to overwrite your first Public Key. Remember that scp command will overwrite authorized_keys files and should not be used.
ssh-copy-id -i $HOME/2nd-station/id_rsa.pub linxadmin@VPS-IP-ADDRESS
Method2 – Using Native Linux/UNIX Commands
Note: If you are using a Linux/UNIX machine that doesn’t have Open-SSH package installed, hence ssh-copy-id command can’t be used, then you can use Native Linux/UNIX commands.
Again, replace linuxadmin user using the Admin account you suppose to use, specify the 2nd public key path location, and replace VPS-IP-ADDRESS using the VPS IP Address.
cat $HOME/2nd-station/id_rsa.pub | ssh linuxadmin@VPS-IP-ADDRESS cat >> $HOME/.ssh/authorized_keys"
2. You will be prompted by Authenticity Message
The authenticity of host 'VPS-IP-ADDRESS(VPS-IP-ADDRESS)' can't be established. ECDSA key fingerprint is 0f:d4:22:d8:82:cb:54:b4:57:c1:8d:90:97:7c:05:5d. Are you sure you want to continue connecting (yes/no)?
The SysAdmin should have sent you both ECDSA and RSA Fingerprints. Retrieve the email you received from the SysAdmin to verify the first 2 and last 2 digits of ECDSA Key fingerprint before typing Yes.
3. Enter Your Private Key’s Passphrase
After you have verified the Server’s Key ECDSA fingerprint, type Yes to continue. You should be prompted to enter your Private Key’s Passphrase (this private key is the pair of the public that has been added by the SysAdmin).
Once you enter the passphrase, the upload or copy process will start, and once it’s done, you will see the following message. This message indicates that the upload/copy of your second or even third public key has been successful.
Now try logging into the machine, with "ssh 'linuxadmin@VPS-IP-ADDRESS'", and check in: ~/.ssh/authorized_keys to make sure we haven't added extra keys that you weren't expecting.
5. SSH to the VPS from the 2nd Station
After uploading your 2nd Public Key from the first station, SSH this time from the your 2nd station to verify that you had successfully uploaded the 2nd Public Key. You should be prompted to Enter your Private Key’s Passphrase as shown below.
ssh linuxadmin@VPS-IP-ADDRESS
Since you have uploaded the Public key at step1, you should be prompted to enter Private Key’s Passphrase to login.
Enter passphrase for key '/your-user/.ssh/id_rsa': The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Fri Jun 12 11:54:49 2015 your-user@station2:~#
6. Display authorized_key file
At the VPS side, display all linuxadmin’s Public Keys to see how you have appended the 2nd Public on its new line. Remember, always add a comment while creating SSH-keys, since it will make it easy to distinguish between Public Keys.
cat /linuxadmin/.ssh/authorized_keys
Subject Related
By Wikipedia SSH | About SSH | Debian HowTo SSH-Keys | CentOS HowTo SSH-Keys
Building Professional Web Hosting Solution
<< Linux Basic Setup and Configuration Course
>> Configuring SSH-Key Based Authentication Section
- Understanding SSH-Keys Based Authentication
- Creating SSH-Keys using Putty Keys Generator
- Creating Public VPS Droplet using DigitalOcean
- Managing Linux VPS Instance via Putty SSH Client
- Managing Linux VPS Instance via WinSCP Client
- Creating SSH-Keys using Terminal Keys Generator
- Switching SSH Password to SSH-Keys Authentication
- Uploading Admins and Friends SSH-Keys to VPS
- Uploading SSH Public Keys using VPS Panel
- SSH Hopping using SSH Agent Forwarding
- Deploying Public VPS instance using Vultr Provider
- Securing and Hardening SSH Server Configuration
- SSH Server and Client Most Known Error Messages
LEAVE A COMMENT